Inside Russia’s secret digital war on NATO’s logistics lifeline to Ukraine

Since March 2022, Russia’s military intelligence quietly infiltrated NATO supply chains. A report shows how amid Moscow’s ongoing invasion of Ukraine, Russia’s GRU military intelligence blended into infrastructure, turning Poland’s logistics points and border crossings into a live surveillance feed of the military aid for Ukraine. This is according to a report by Polish authorities, issued in late May.
The findings confirm that Russia’s 85th Main Special Service Centre — known as Unit 26165, or APT28 (also referred to as Fancy Bear) — carried out targeted cyberattacks aimed at monitoring Western military support for Ukraine.
Release exposes GRU campaign
The report was issued by Poland’s Military Counterintelligence Service (SKW) and the Internal Security Agency (ABW). It was “authored or endorsed” by cybersecurity and intelligence agencies from the United States (NSA, FBI), United Kingdom (National Cyber Security Centre), Germany (Federal Intelligence Service and Federal Office for Information Security), France, Canada, Estonia, the Netherlands, Czech Republic, and others.
The report says that GRU unit 26165’s cyberespionage operations have struck Western logistics and tech sectors, affecting numerous government, private, and commercial organizations across multiple domains.
Russia’s state-sponsored cyberespionage campaign exploited vulnerabilities in commercial and government systems, hacked thousand private and public IP cameras across at least 13 countries — particularly at border crossings and logistics hubs — and compromised sea, air, and rail transport, logistics center operations, and even air traffic management.
“The services and agencies authoring this publication assess that these activities will continue in the future in a similar form and manner, using comparable techniques,” the report warns.
The purpose of the report is “to warn potential victims and provide them with recommendations to help strengthen their protection against threats.”
Logistics targeted
The GRU obtained information about delivery routes and dates, transshipment locations, and the details of senders and recipients of military equipment, aiming to “gain operational knowledge that can be used against Ukraine and its partners.”
Targeted entities across NATO, Ukraine, and international partners include:
- The defense sector
- Transportation and logistics hubs and centers (e.g., ports, airports)
- Maritime infrastructure
- Air traffic management
- IT service providers

Pro-Palestinian activists cause $ 1.1 mn damage to Ukraine-bound military vehicles in Belgium
Tactics: Phishing, Malware, and Surveillance Hijacking
According to the report, GRU hackers exploited known software vulnerabilities and conducted spearphishing campaigns—targeted email attacks crafted to appear as legitimate messages from trusted institutions. These emails impersonated government agencies, logistics firms, and cloud service portals, and were tailored to specific organizations to trick recipients into revealing their login credentials.
Once inside, they exploited known software vulnerabilities, including:
- Microsoft Outlook (CVE-2023-23397)
- WinRAR (CVE-2023-38831)
- Roundcube Webmail (CVE-2020-12641, CVE-2020-35730, CVE-2021-44026)
Malware including HEADLACE, MASEPIE, and tools like Impacket and PsExec were used to maintain persistent access. Attackers elevated privileges, collected credentials, exfiltrated files, and altered email permissions to intercept internal communications for a long period of time without detection.
In some instances, they used “legitimate but vulnerable applications” such as IT remote support tools to move laterally through victim networks.
Working in coordination with CERT Polska – the Polish computer emergency response team – and international partners, SKW also identified and blocked GRU activity targeting software supply chains.
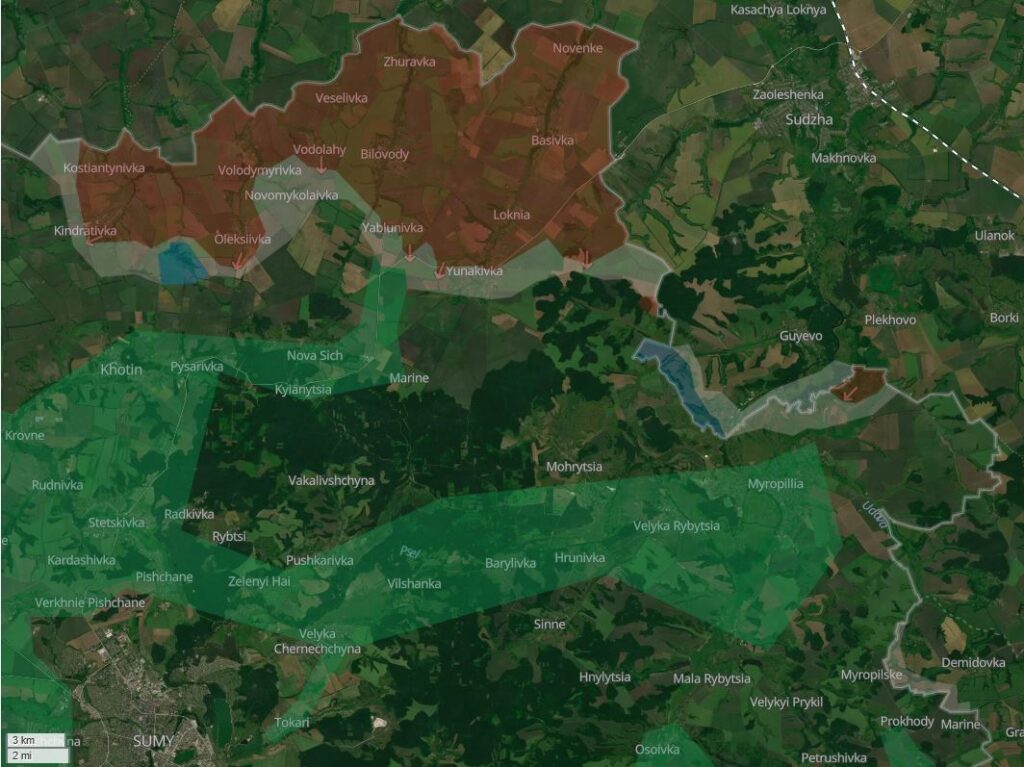
Real-Time Tracking Through Civilian IP Cameras
One of the most striking aspects of the campaign was its use of hijacked IP cameras — both public and privately owned — to monitor aid shipments in real time. According to the report, since March 2022, Russian hackers targeted over 10,000 internet-connected cameras in Ukraine, Poland, Slovakia, Romania, and other nearby countries.
These devices were accessed via default or weak credentials and streamed through protocols like RTSP (Real-Time Streaming Protocol), often without the owners’ knowledge.
Footage was then likely analyzed to track the movement of military convoys, humanitarian aid, or strategic cargo.

Germany says Russia behind massive cyberattack last year after Berlin decided to send Ukraine tanks
Widespread Targets: From Military Firms to IT Providers
The report says entities impacted included:
- Logistics and freight companies involved in transporting military equipment
- Air traffic management and radar communication services
- Ports
- IT services
- Defense sector and “at least one entity involved in the production of control systems (ICS) and railway line management“
- Public and private cameras, with device owners unaware of unauthorized access
Victims were identified in Poland, Ukraine, the United States, Germany, France, Italy, Bulgaria, Romania, Slovakia, and others.
Operational depth: GRU maintained long-time presense in the system
The GRU’s access was persistent and often invisible. In compromised systems, attackers manipulated:
- Email inbox permissions to silently forward mail to external servers
- Domain controllers and Active Directory databases
- Scheduled tasks and Windows registry keys to maintain malware execution
- Local administrator privileges to gain full access to system tools
Authorities say the GRU’s campaigns involved the exfiltration of sensitive data, including files, email messages, and information about shipments and transport routes related to aid deliveries to Ukraine.
Global coordination — and a warning
The report includes over 40 pages of technical guidance, urging all organizations — particularly in transport, logistics, IT, and surveillance sectors — to:
- Immediately patch known vulnerabilities
- Enforce multifactor authentication and least-privilege policies
- Audit remote access software and email forwarding rules
- Disable insecure protocols like Telnet, SMBv1, and RTSP where not essential
- Secure IP cameras with updated firmware and unique credentials
Poland’s final message: assume you’re a target
The reports has called on both public and private-sector entities to assume “that they are of interest to the GRU” and adopt zero-trust postures across networks.
“Cyberspace is now a real battlefield for national security. GRU activities target public institutions, companies, and citizens. We must speak out about this so that no one is surprised when they fall victim. It is our duty to inform, warn, and build resilience—together, across borders,” said Poland’s Minister of Digital Affairs Krzysztof Gawkowski in a statement regarding the report.








 ” Wild Hornets wrote in the video caption, which indicates it remains in the testing or pre-approval stage.
” Wild Hornets wrote in the video caption, which indicates it remains in the testing or pre-approval stage.

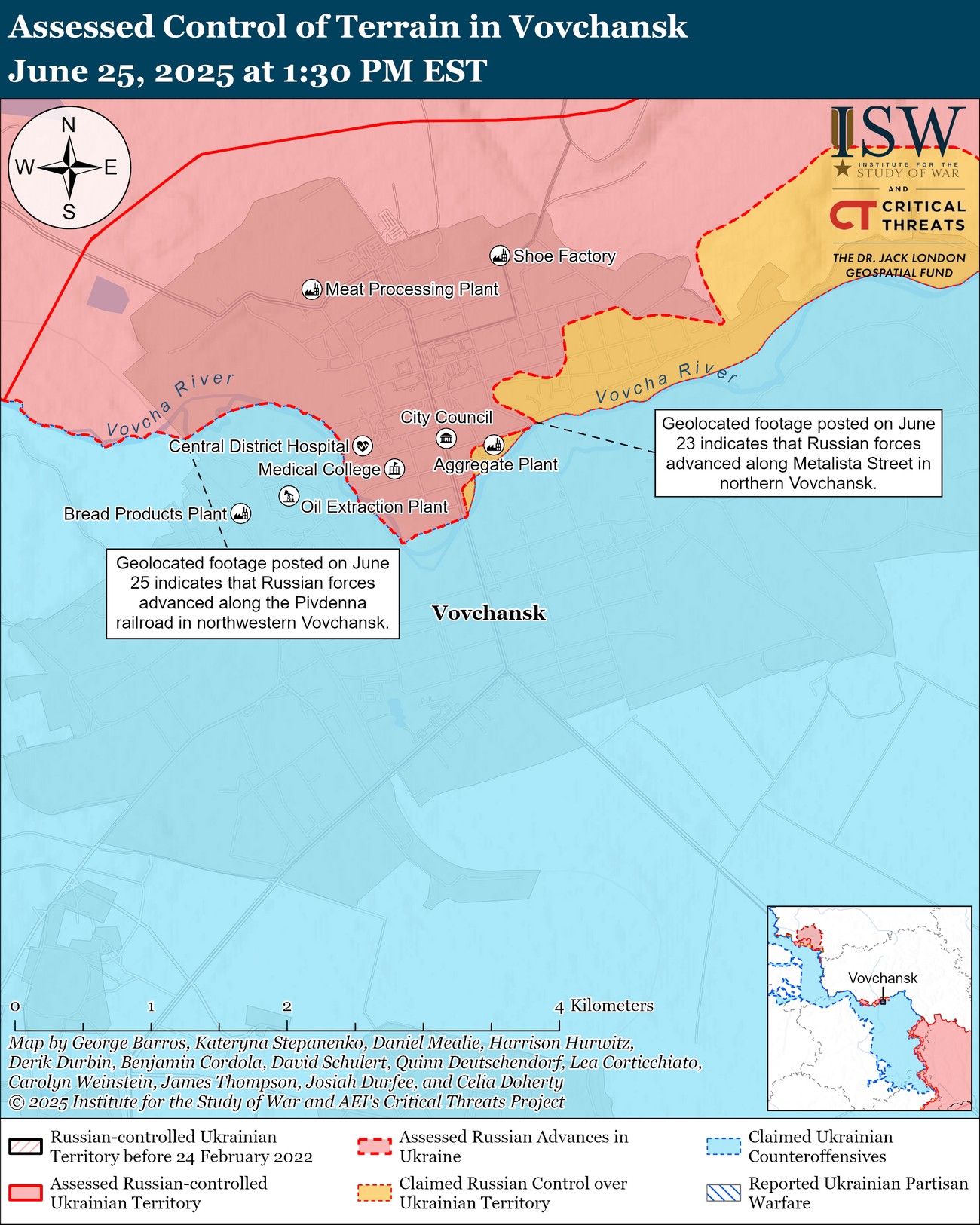

























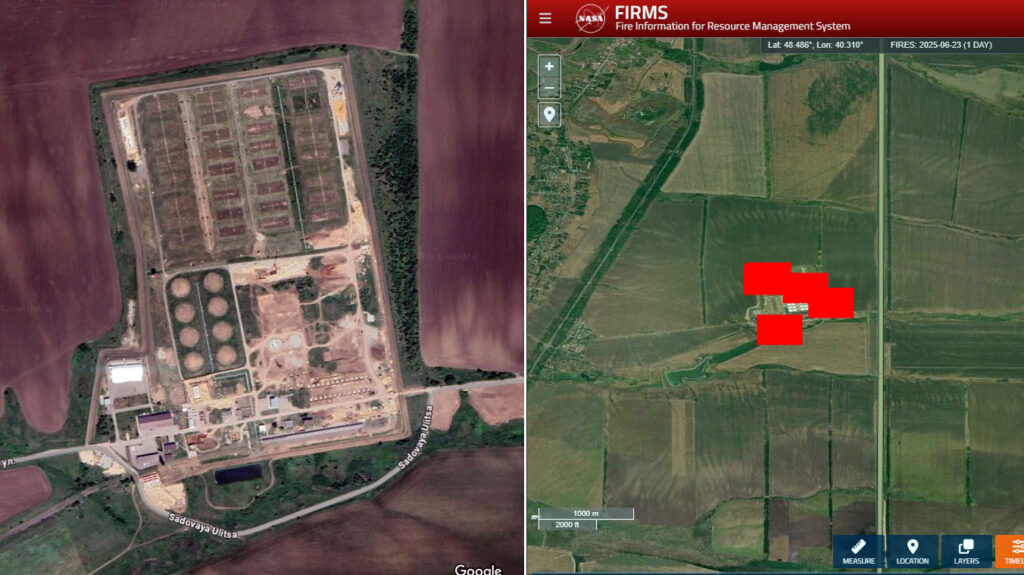
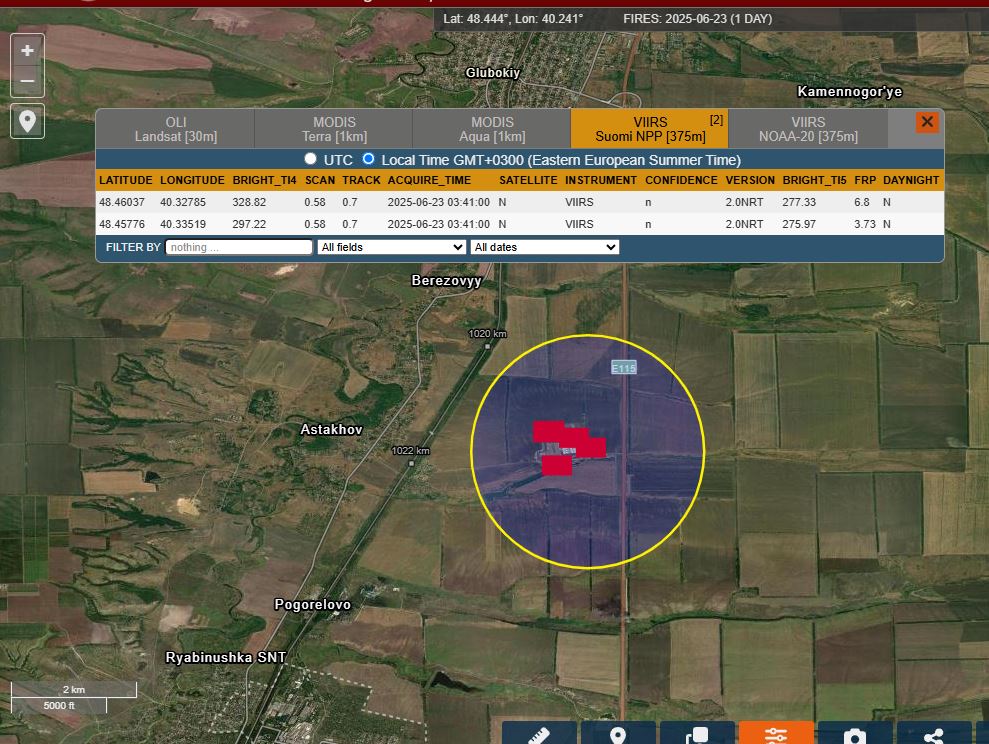





 TG/HUR, Andriushchenko Time
TG/HUR, Andriushchenko Time 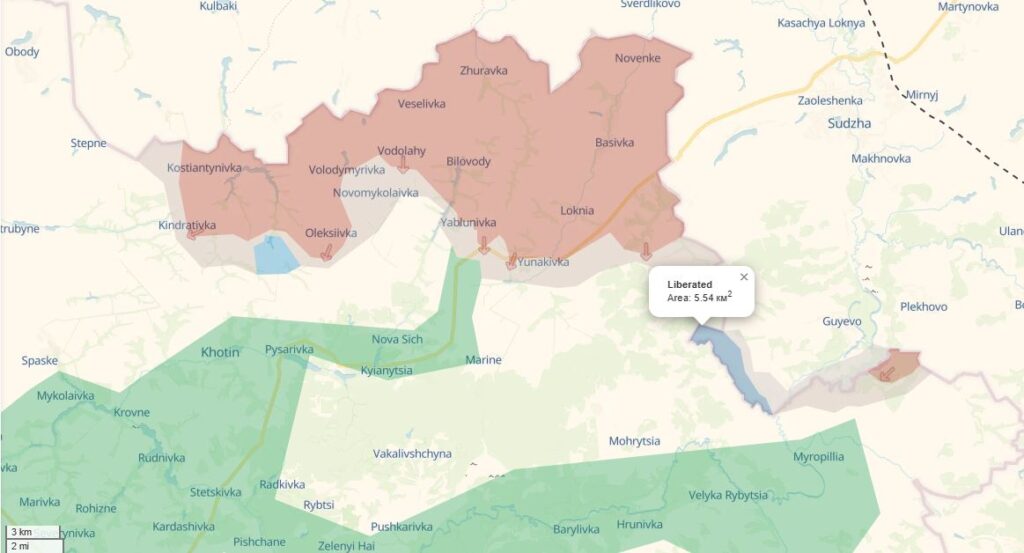

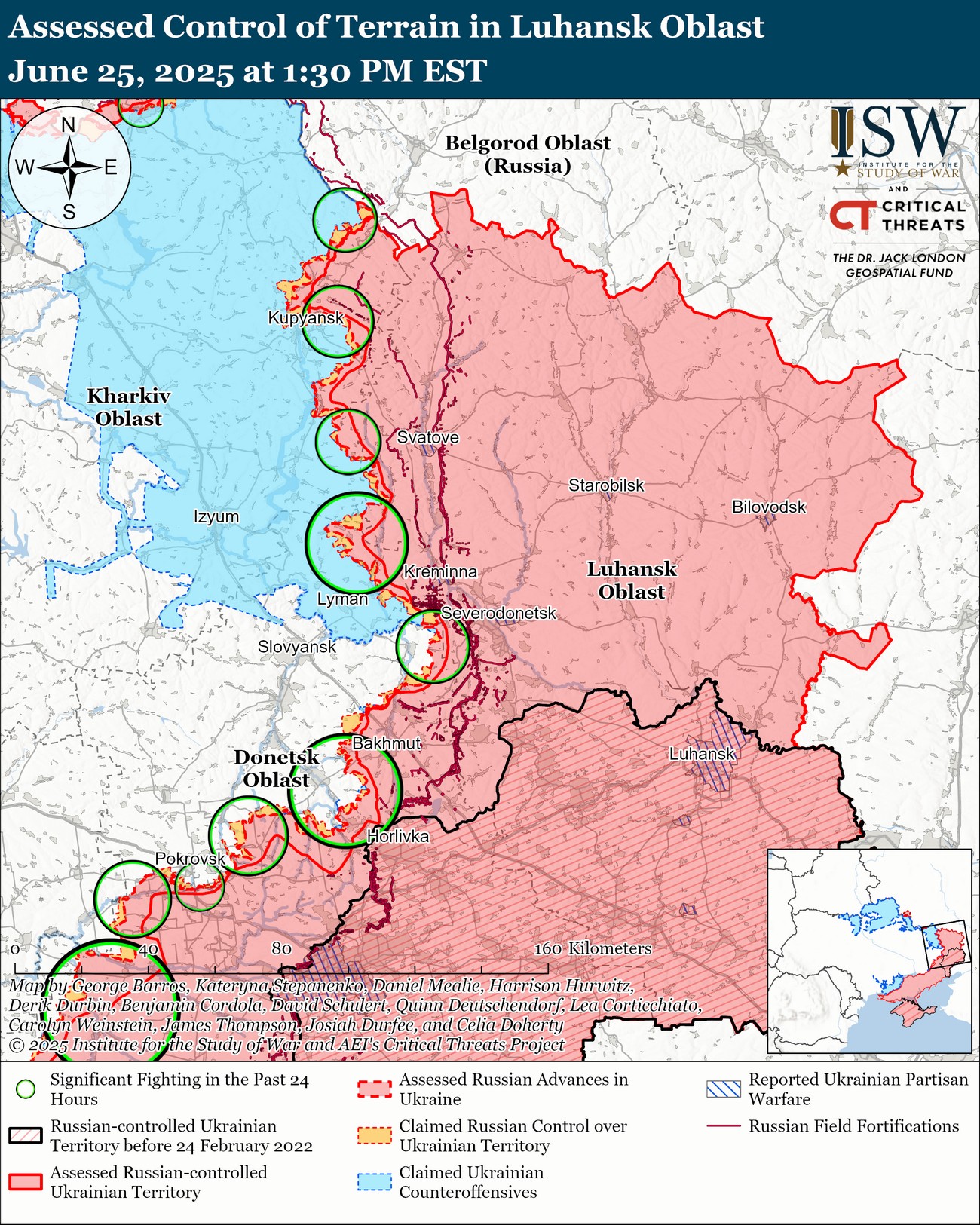
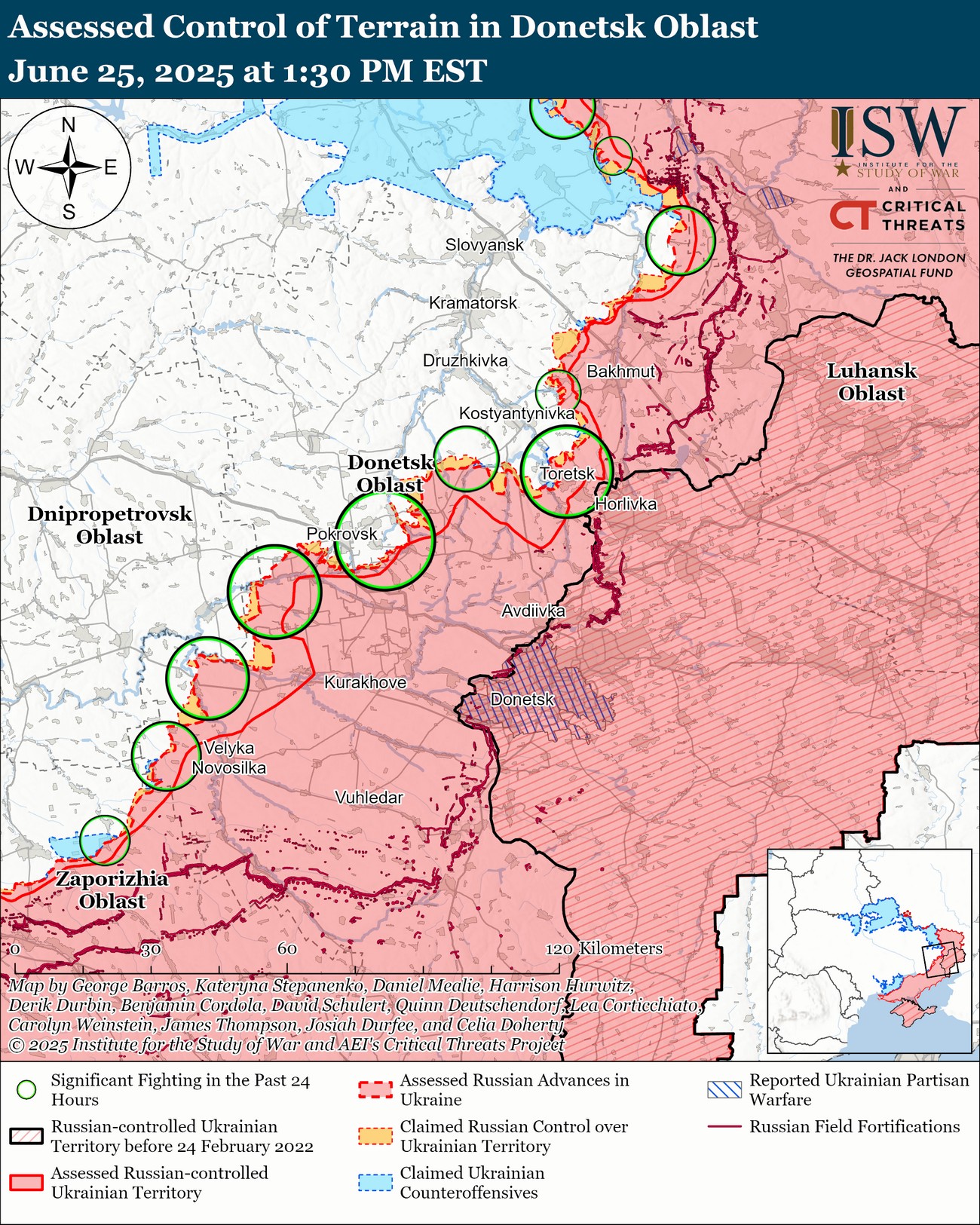
 UA_REG TEAM of the 8th Separate Special Purpose Regiment confirms, among hitting other heavy equipment and personnel, the destruction of a Russian 1L219 "Zoopark" counter-battery radar.
UA_REG TEAM of the 8th Separate Special Purpose Regiment confirms, among hitting other heavy equipment and personnel, the destruction of a Russian 1L219 "Zoopark" counter-battery radar.