Ukraine’s agricultural imports up by 10% in H1 2025 – IAE






Your smartphone probably has more computing power than the drone that woke Ukrainian families at 3 AM this morning. Yet these cheap weapons have become Putin’s most reliable tool for terrorizing Ukraine—and they’re multiplying faster than anyone expected.
Russia launched more than 728 drones in a single night attack on 9 July 2025. In June alone, 5,483 drones targeted Ukraine—16 times more than June 2024 and a 30% increase over the previous month. Compare that to September 2022, when Russia’s entire monthly arsenal was just 40 units.
According to Ukrainian President Volodymyr Zelenskyy, Russia has launched 28,743 drones at Ukraine since February 2022. The escalation has been systematic: 40 drones in September 2022, increasing to 5,483 by June 2025—a 137-fold increase over 33 months.
What changed?
A German aviation engine from the 1980s, now manufactured in China and smuggled to Russia.
The Shahed-136 represents a shift in modern warfare—establishing what defense analysts call asymmetric warfare through large-scale, low-cost swarm attacks. Iran’s HESA reverse-engineered a 1980s German design (the Die Drohne Antiradar) to create a flying bomb that carries 118 pounds (53 kg) of explosives over 1,000 miles (1,600 km).
Iran initially sent combat drones to Russia on 19 August 2022—both Mohajer-6 surveillance drones (200km range, two missiles per wing) and Shahed kamikaze units. Tehran and Moscow officially denied the transfers, but Iran later acknowledged them while claiming they predated the invasion.
In early September 2022, IRGC Commander Major General Hussein Salami noted that Iran was selling domestic military equipment to foreign buyers, including “major world powers,” and training them to use this equipment.
But the real game-changer came with Iran’s $1.75 billion technology transfer deal that gave Russia the blueprints, software, and production technologies to build its own versions. Shahed drones were previously built by Shahed Aviation Industries in Iran, where allegedly every drone factory has two backup sites in case of aerial attacks.

Russia’s drone production centers on the Alabuga Special Economic Zone in Tatarstan—more than 1,300 kilometers from Ukraine’s border and Russia’s most successful SEZ, accounting for 68% of total revenue. The facility produced 2,738 Shahed-style drones in 2023, then more than doubled to 5,760 units by September 2024.
Recent analysis suggests Russia produced over 10,000 drones in 2024 alone, doubling monthly production from 1,000 to nearly 2,000 units.
The original contract called for 6,000 drones by September 2025—a target the facility appears to have exceeded well ahead of schedule.
Satellite imagery shows at least eight new warehouse structures under construction. The Institute for Science and International Security estimates Alabuga now produces almost 20 drones per working day—double the original contract rate. Russia initially predicted production costs of $48,000 per Geran-2 (25% of the purchase cost), but by April 2024 this increased to around $80,000 due to upgrades. The original plan called for 310 drones per month with 24-hour operations, plus plans for an additional 6,000 drones per year after the initial contract.
The main structural components requiring sophisticated supply chains are the airframe (fuselage), engine, avionics (electronics), and combat unit.
Russia started with a three-phase plan:
Phase 1 was reassembling 100 drones per month from Iranian knock-down kits.
Phase 2 would produce their own airframes.
Phase 3 would produce another 4,000 drones by September 2025 with little Iranian help.
Alabuga Machinery LLC completed construction of production buildings in December 2022 and sent its first team of specialists to Iran for training in March 2023. In parallel, the process of assembling drones from Iranian machine kits continued.
But there were problems. About 25% of Iranian kits arrived damaged or broken—including one dropped during delivery.
Here’s the interesting part: leaked data shows 90% of Iranian Shahed-136’s computer chips and electrical components are manufactured in the West, primarily in the United States.
So even “Iranian” drones are mostly Western technology.
Iran initially helped Russia with direct connections. According to the US Treasury Department, Alabuga requested meetings with Mado Company officials (Iranian drone engine producers) and received detailed documents on the MD550 engine that powers the Shahed-136. Iran’s Defense Ministry also facilitated the supply of UAV parts, models, and ground stations to Alabuga through UAE-based Generation Trading FZE.
What makes this surge possible? A Chinese supply network that signed contracts worth 700 million yuan ($96 million) with Alabuga between September 2023 and June 2024. Thirty-four Chinese companies partnered with the facility during this period.

Here’s where it gets interesting. The heart of Russia’s drone program is a Limbach L550E engine—originally designed by German company Limbach Flugmotoren in the 1980s. Iran reverse-engineered this decades ago. Now, Chinese company Xiamen Limbach Aircraft Engine Co. manufactures these engines and ships them to Russian weapons factories.
Xiamen Limbach is wholly owned by Fujian Delong Aviation Technology Co., which also owns the original German Limbach Flugmotoren GmbH—one of the world’s leading manufacturers of aircraft piston engines engaged in both development and maintenance. The engines don’t go directly to Russia—they flow through intermediary companies that act as buffers between IEMZ Kupol and Chinese suppliers.
Between November 2023 and October 2024, Russian intermediary TSK Vektor LLC imported $32.8 million worth of components from Chinese suppliers: aircraft engines, computer parts, electrical equipment, transistors, electronic modules, connectors, plugs, sockets, spare parts, and components.
The broader Chinese supplier network with specific roles includes:
Most label exports as “for general civil purpose” or “for general industrial purpose” to avoid detection.
When Reuters reported the Chinese engine connection in September 2024, the US and EU sanctioned several companies, including Xiamen Limbach. The EU also suspects Xiamen Limbach may have passed L550 engine drawings directly to Iranian Shahed-136 manufacturers.
But Beijing Xichao International Technology and Trade immediately took over L550E shipments.
The engines now travel from Beijing to Moscow to Izhevsk, labeled as “industrial refrigeration units.”
Engines are shipped to Russian front company SMP-138 (registered under Abram Goldman), then forwarded to LIBSS. The contract explicitly states engines will be described as cooling units because of their sensitivity.
Russia hasn’t just copied Iran’s design. The Garpiya-A1 (“Harpy”), manufactured by IEMZ Kupol (part of Almaz-Antey), closely resembles the Shahed-136 but uses Chinese L550E engines and unique bolt-on fins. Russia’s Defense Ministry signed a 1 billion ruble contract ($10.9 million) with IEMZ Kupol in early 2023 to develop the drone factory.
Between July 2023 and July 2024, Russia produced more than 2,500 Garpiya-A1 UAVs. IEMZ Kupol signed a contract to produce more than 6,000 Garpiya drones in 2025, up from 2,000 in 2024, with more than 1,500 delivered by April 2025. Ukrainian intelligence reports about 500 Garpiya drones are launched monthly.
Russia has shifted from using Iranian “M” series Shaheds to producing its own “K” and “KB” variants since 2023, indicating full domestic production capability. Conflict Armament Research, a British weapons-tracking group, examined downed drones and confirmed Russia is now producing its “own domestic version of the Shahed-136.”
But Russia’s cleverest innovation is the Gerbera drone—a foam and plywood decoy that costs one-tenth the price of a real Shahed but appears identical on radar. It forces Ukrainian air defenses to waste expensive interceptor missiles on worthless targets while real attack drones slip through. Russia planned to produce 10,000 Gerberas in 2024—twice the number of actual attack drones.
Russia also produces the Geran-3, a jet-powered variant with higher speeds for faster targeting and better evasion of antiaircraft systems.
How does Alabuga staff this massive operation? Through questionable recruitment that raises human rights red flags.
They planned for 810 staff working in three shifts to run the facility 24/7. The facility employs over 1,000 women from across Africa, recruited through Alabuga Start with promises of $550 monthly salaries, subsidized housing, and educational opportunities. The recruitment campaign in Uganda’s capital, Kampala, specifically targeted young female students. Management seizes passports to prevent workers from quitting—basically forced labor.
The factory also employs Russian students as young as 15 through local polytechnic colleges, including Alabuga Polytech. As of August 2023, several hundred 15‑year‑old students worked at Alabuga Polytech under “work experience programs,” with employers promising wages up to 70,000 rubles/month (around US $700)— roughly 20–30 % higher than typical monthly earnings in Tatarstan.
The Shahed builders were disturbed about building weapons for the war against Ukraine, so Alabuga keeps hiking salaries. Some workers now earn ten times the median Russian wage.
US Treasury sanctions specifically cited Alabuga CEO Timur Shagivaleyev for “exploitation of underage students to assemble these UAVs.”
How does Russia pay for Chinese technology? Russia built a network that avoids the banking system and instead pays with gold bars, commodities, and barter deals.
Iran’s pricing changed through negotiations. Initially, Iran wanted approximately $375,000 per drone. Final deals settled at either $193,000 per unit for orders of 6,000 drones or $290,000 for orders of 2,000 units.
In February 2023, Alabuga Machinery allegedly transferred 2,067,795 grams of gold bars to Iranian proxy company Sahara Thunder as payment for components—more than 2 tons of gold signed off by CEO Shagivaleyev.
Sahara Thunder was later sanctioned by OFAC in April 2024 for supporting Iran’s Defense Ministry and facilitating UAV transfers. The company was identified as a front for Iran’s military, also shipping commodities to China and Venezuela.
The total contract value reached $1.75 billion through gold transfers, barter arrangements, and commodity swaps designed to circumvent Western sanctions.
Chinese component supply shows the real problems with current sanctions. Despite China’s export control law supposedly preventing dual-use technology transfers, there are obvious gaps in prohibited classification codes that allow systematic workarounds. Export control measures don’t match actual dual-use risks, so Russian manufacturers keep getting critical technologies despite formal bans.
When the US and EU sanctioned Xiamen Limbach in October 2024, Beijing Xichao International Technology took over shipments within weeks. This rapid substitution suggests pre-existing networks designed to maintain supply continuity.
Chinese suppliers have developed sophisticated systems to disguise military components. According to European security officials, engines are shipped as “industrial refrigeration units,” electronic components as “general civil purpose” items, aircraft parts as “general industrial equipment.” This “cooling units” description enabled goods to be exported without alerting Chinese authorities.
Sanctioned entities include:
But when one Chinese company gets blacklisted, another replaces it within weeks.
Secondary sanctions targeting third-party companies have proven insufficient. Chinese companies face limited consequences for supplying Russian defense contractors, and new entities can be established faster than sanctions regimes can identify them.
This collaboration shows how authoritarian states can create integrated defense partnerships that bypass Western sanctions. The partnership has built covert payment networks involving gold transfers and middleman countries that make enforcement harder.
A new Deng Xiaoping Logistics Complex being built near Alabuga will handle 100,000 containers annually via direct rail links between Russia and China, suggesting broader military cooperation.
The psychological impact goes beyond military effectiveness. These weapons target civilian infrastructure—power plants, hospitals, schools, apartments—designed to wear down Ukrainian society through constant air raids. Ukrainian families spend nightly hours in bomb shelters, kids sleeping in bathtubs to avoid strikes.
The weapons strain Ukrainian air defenses in critical ways. Ukraine intercepts most drones, but the cost equation favors attackers: a $500,000 interceptor missile destroys a $50,000 drone. If attacks continue at current intensity, this creates unsustainable resource imbalances that could overwhelm air defense systems through economic attrition rather than penetration.
If Russia can produce 10,000+ attack drones annually using Chinese components and Iranian designs, similar capabilities could threaten NATO members.
The weapons represent cost-effective methods for sustained attacks against civilian infrastructure across Europe, potentially overwhelming air defense systems through sheer volume.
European officials have urged China to tighten export controls, with EU foreign policy chief Kaja Kallas warning Chinese Foreign Minister Wang Yi that Chinese firms’ support threatens European security. Beijing denies knowledge of military applications while maintaining its right to trade with Russia under international law.
Current sanctions haven’t worked to stop this supply chain. China has become the key enabler—Ukrainian intelligence reports that every critical component (engines, navigation systems, control units) comes from Chinese manufacturers.
What needs to change:
Better coordination: Allies need to align sanctions policies targeting both Russian UAV manufacturers and Chinese suppliers. Right now, sanctions are scattered and don’t deter anyone.
Hit Chinese companies harder: Aggressive secondary sanctions against Chinese manufacturers and their parent companies who help transfer technology to Russia. This includes targeting banks that enable these deals.
Close export loopholes: Tighten control over dual-use technology exports from China, close gaps in prohibited classification codes that currently allow systematic workarounds. Better coordination between customs and intelligence agencies to catch evasion attempts.
Pressure Beijing financially: Enhanced diplomatic pressure on Beijing to stop Chinese firms from transferring critical technologies that enable weapons production. This includes targeting gold-based payment networks and commodity swap deals.
Share intelligence better: Better intelligence coordination between allies to track emerging supply chains and identify new middleman companies before they get established.
The drone attacks hitting Ukraine carry Chinese engines, Iranian designs, and Russian assembly. They’re a test case for whether economic isolation can work in a connected global economy. So far, determined state actors with willing partners can get around almost any restriction.
Whether Western governments can adapt their systems to match evasion network sophistication is still an open question. The answer will decide not just Ukraine’s fate, but whether economic tools can actually deter international aggression.


Trump has threatened new sanctions if Moscow does not agree to end the war by Friday

© Copyright 2025 The Associated Press. All rights reserved

On the occupied peninsula, Russia’s repressive machine sees the Ukrainian flag as a greater threat than the swastika. According to the civil organization Crimean Process, in the past six months in occupied Crimea, there have been three times more court cases against supporters of Ukraine than against individuals promoting Nazi symbolism.
Moreover, 56% of all cases related to the display of banned symbols involved pro-Ukrainian citizens.
“People who demonstrate pro-Ukrainian views are not only prosecuted more frequently, but also subjected to humiliation, fabricated charges, and moral pressure through propaganda in the media,” the report states.
Of 96 cases analyzed under Article 20.3 of Russia’s Code of Administrative Offenses, the largest share of charges were directed at Ukrainian sympathizers.
26% of “Ukrainian” cases resulted in arrest, while none of the criminal subculture defendants were imprisoned. Nearly half of the cases against Ukrainians included additional charges, such as hooliganism or “discrediting the army.” In contrast, not a single case involving Nazi symbols included such add-ons.
“Any manifestation of Ukrainian national identity, patriotism, or resistance to occupation is viewed by Russian authorities as a threat to ‘stability’ and ‘security,’” human rights activists say.
In addition, judges in “Ukrainian” cases more frequently violate procedural norms:
Human rights defenders stress: this is selective justice, where patriotism is punished more harshly than overt hate.






The Kremlin again threatens Europe with missiles. The Russian Foreign Ministry has announced that the country is lifting its self-imposed restriction on the deployment of land-based ballistic and cruise missiles with a range between 500 and 5,500 km, according to Radio Free Europe/Radio Liberty.
Once-banned missiles are back on the table. In 1987, the US and USSR agreed to eliminate all missiles of this class, but in 2019, the treaty formally expired. After that, Russian President Vladimir Putin claimed Russia would not be the first to deploy such missiles unless the US did so first.
Now, Moscow reverses course: it has lifted the restriction, blames the West, and claims a threat from American missiles in Europe and the Asia-Pacific region. The official reason: “steps by the collective West” that, according to the Kremlin, “destabilize the situation in border regions.”
“The Russian Foreign Ministry acknowledges the disappearance of conditions for maintaining the unilateral moratorium on the deployment of such weapons,” the statement says.
Western states already claimed in 2019 that Russia had de facto violated the agreement — the main evidence being the 9M729 missile system, which, according to the US and NATO, has a range exceeding 500 km.
Moscow denies it, but reality suggests otherwise: the missiles exist, and now the Kremlin officially admits it is ready to deploy them. This move threatens to spark a new arms race and escalate security risks not only for Ukraine but for all of Europe.
In November 2024, Russia launched a 9M729 missile at the city of Dnipro, marking the first confirmed combat use of the controversial system, also known by the codename “Oreshnik”. The missile was equipped with six warheads, each capable of independent targeting. The extent of damage remains undisclosed.



A powerful explosion cut power to the Russian military base in Zaporizhzhia Oblast late on 3 August. The blast temporarily occupied the city of Berdiansk and destroyed a power substation that supplied electricity to the base located at the former Berdianski Zhnyvarky factory, UkrInform reports, citing its source in Ukraine’s Defense Intelligence.
Since the start of Russia’s all-out war in 2022, Berdiansk has remained under occupation. The city has suffered extensive destruction, water and power outages, explosions at the port, and an aggressive campaign of Russification, including persecution of citizens with pro-Ukrainian views.
The energy strike triggered a fire, disabling a key element of the occupiers’s logistics infrastructure.
According to Ukraine’s Defense Intelligence, the explosion and ensuing fire disabled transformers that powered the facility where Russian troops repaired military vehicles and stored weapons.
“The final consequences of the explosion and the extent of the damage are still being clarified,” says Defense Intelligence source.
Local residents were the first to report the powerful blast, posting videos and photos on social media. The surrounding streets lost power, and social media posts confirmed the fire at the substation.
After the capture of Berdiansk, Russian occupying forces converted the plant’s workshops into a repair hub, arms depot, and barracks. Damaged vehicles from the front were brought here for repairs before being sent back to the battlefield.
The destruction of the facility’s power supply seriously disrupts the occupiers’ logistics and hampers their ability to repair equipment.



Six individuals have been served with notices of suspicion for involvement in a corruption scheme involving the procurement of military equipment, reports the National Anti-Corruption Bureau of Ukraine (NABU).
This is the first major report by Ukraine’s anti-corruption agencies since a controversial law restricting their independence was signed and later reversed after street protests.
According to the report, among the suspects are government and military officials, as well as executives from drone manufacturing companies.
NABU and the Specialized Anti-Corruption Prosecutor’s Office (SAPO) say they have exposed a “large-scale corruption scheme in the procurement of UAVs and electronic warfare systems” operating during 2024-2025.
According to NABU, the suspects systematically embezzled funds from local government budgets that had been allocated to the Defence Forces.
President Zelenskyy has reportedly dismissed four officials from their posts since the notices were served.
NABU identified the six suspects as:
On 2 August, 2025, NABU and SAPO reported their findings to Zelenskyy. The scheme allegedly involved a sitting member of Zelenskyy’s Servant of the People party, whose faction membership was dismissed that day. Dismissals of the local government and military officials followed on the same day.
This report comes shortly after attempts by the Ukrainian government to stifle the work of the national anti-corruption agencies. A controversial bill restricting NABU and SAPO’s autonomy was recently passed by parliament and signed into law by Zelenskyy.
This decision sparked nationwide protests. Within 4 days, Zelenskyy submitted a draft bill to reverse the restrictions and restore the agencies’ independence.
This is NABU and SAPO’s first major investigation report since this incident that brought renewed attention to the importance of Ukraine’s anti-corruption organizations.

Ukraine will take another step toward the safe de-occupation and clearing of war remnants. On 4 August, Ukraine’s Ministry of Defense announced that sappers from the Ukrainian Armed Forces and the State Special Transport Service will be trained at the Regional School for Humanitarian Demining at the Lebanese Mine Action Center.
As of August 2025, Ukraine is the most mined country in the world. Official data shows that over 139,000 square kilometers of Ukrainian territory are potentially contaminated with mines and explosive ordnance, amounting to nearly 40% of the entire country.
The program will be funded by the French government. Lebanon was chosen due to its extensive experience in post-conflict land clearance.
“We thank the Government of the French Republic and the French people for their support in the fight against the Russian aggressor,” says Colonel Ruslan Berehulia, head of the Main Department for Mine Action.
Agreements were reached during a Ukrainian delegation’s visit to France, where Defense Ministry representatives met with:
They discussed:
The French side confirmed its ongoing commitment to support Ukraine not only financially, but also through:
This partnership strengthens Ukraine’s ability to clear liberated territories and reduce civilian risks in the long term.



Some 140 German investigators have conducted large-scale raids at Spinner, a high-precision machine tool manufacturer suspected of knowingly supplying equipment to Russia’s military industry. Three individuals have already been charged with violating sanctions.
In 2023, Ukrainian anti-corruption bodies urged German authorities to halt exports of Spinner’s high-precision machines to Russia via Türkiye. One such CNC machine was reportedly produced for a Russian factory producing high-explosive fragmentation shells for use in Ukraine.
German law enforcement searched Spinner Werkzeugmaschinenfabrik GmbH’s offices in several German cities and abroad. Eight prosecutors were involved in the investigation.
According to the investigation, the company may have knowingly sold 20 machines to Russia for a total of €5.5 million, despite the sanctions.
Despite the company’s claims about “compliance systems” and “lack of knowledge” about the end user, investigators say otherwise. Sources indicate the deliveries may have gone through third countries, particularly Turkiye, Bloomberg reports.
“Sanctions enforcement must work like this — with documents, equipment seizures, and court proceedings,” experts say.
Circumventing sanctions is now a criminal offense in the EU, meaning those found guilty could face prison time, not just fines.


India has started buying American, Canadian, and Middle Eastern oil, but has not abandoned Russian supplies. The country’s giant Indian Oil Corp has recently purchased 7 million barrels of oil, Reuters reports.
Russia remains India’s main oil supplier, accounting for about 35% of total imports. Moscow’s energy exports remain its leading source of profits, which it uses to fund its war against Ukraine.
According to the latest findings, India’s largest oil refining company has bought 4.5 million barrels of American oil, 500,000 barrels of Canadian Western Canadian Select, and 2 million barrels of Das crude from Abu Dhabi. The delivery is scheduled for September 2025.
These large purchases are connected to the country’s intention to replace Russian oil due to falling discounts and new EU sanctions on Russian energy.
Earlier, Oil Minister Hardeep Singh Puri said India was ready to meet its oil needs from alternative sources if Russia’s supplies are affected by secondary sanctions.
In July, US President Donald Trump stated that countries continuing to buy Russian oil could face 100% tariffs if Moscow does not agree to a peace deal with Ukraine within at first, 50 days and then 10 days.
NATO Secretary General Mark Rutte confirmed that due to the new economic measures, countries, including India, could suffer losses if they continue to do business with Moscow.

Western weapons production is under threat. China has cut off critical supplies to the US defense industry by restricting access to vital minerals. Companies are delaying deliveries, searching for new sources worldwide, and prices for some resources have skyrocketed 60-fold, The Wall Street Journal reports.
Ukraine depends on Western weapons supplies in Russia’s long-term war of attrition. China is Russia’s closest economic partner and has openly stated that it will not stop supporting Russia’s war machine. Beijing fears that after the war ends, the United Stat will shift its focus to China, and is determined not to let that happen.
In response to the escalating trade war with the US, Beijing tightened export controls on rare earth elements — essential for manufacturing weapons, from drones to fighter jets. Today, China controls about 90% of the global rare earth minerals market. American manufacturers have become dependent on Chinese suppliers.
Companies are already reporting major disruptions. One drone manufacturer had to delay shipments by two months while searching for non-Chinese magnets. Prices for samarium, a mineral needed for magnets that withstand extreme temperatures, have increased 60 times. The mineral restrictions highlight just how dependent the US military is on China.
Since December, China has officially banned exports to the US of germanium, gallium, and antimony — minerals used in machine guns, shells, and night vision devices. Manufacturers are already sounding the alarm.
The CEO of American firm Leonardo DRS stated that germanium reserves are at the limit. This element is critical for infrared sensors in missiles. The company is actively searching for substitutes and new sources.
The Pentagon has ordered a phase-out of Chinese rare earth magnets by 2027, but most companies only have a few months of stock left.
Even alternative routes are failing. In April, Chinese customs in Ningbo detained 55 tons of antimony in transit, which the United States Antimony Corporation was shipping from Australia to its plant in Mexico. After three months, the cargo was forced to return to Australia. Upon arrival, seals were found damaged, and the company is now investigating whether the antimony was contaminated or counterfeit.
Without new sources of mineral extraction, production will inevitably shrink, defense industry representatives warn.

In today’s interconnected world, activists and journalists operating in conflict zones face unprecedented digital threats alongside traditional physical dangers. Modern warfare increasingly includes cyber operations, surveillance technologies, and information warfare tactics that specifically target media professionals and human rights defenders. This comprehensive guide provides essential security protocols and advanced digital defense strategies for high-risk individuals working in or reporting from conflict areas.
Conflict zones have evolved beyond conventional warfare to encompass sophisticated digital operations. Over 60 cyber activist groups launched attacks during the Israel-Palestine conflict alone, while the Russia-Ukraine war has demonstrated how mobile phone tracking can be “implicated in multiple incidents,” including targeted strikes on military personnel. For journalists and activists, this digital dimension creates new vulnerabilities that require specialized defensive measures.
Key threats in modern conflict zones include:
The foundation of secure communication lies in properly implemented end-to-end encryption. Signal remains the gold standard for private communications, with security experts consistently recommending it over alternatives like WhatsApp or Telegram for high-risk scenarios. However, Russia-aligned threat actors are increasingly targeting Signal accounts, making proper operational security crucial.
Best practices for encrypted messaging:
Traditional email platforms are inadequate for conflict zone operations. ProtonMail provides encrypted email services specifically designed for journalists and activists, offering Swiss legal protections and zero-access encryption architecture.
A quality VPN such as Astrill VPN or Proton VPN serves multiple functions beyond basic IP masking in conflict zones. Modern VPNs with threat protection can block phishing websites before users ever see them, while providing essential anonymity for research and communication activities.
Check out the following necessary features in a VPN provider:
Mobile devices present the highest risk in conflict zones due to their tracking capabilities and constant connectivity. Mobile phones can be tracked through multiple methods including military-radio systems and cellular network infrastructure, making proper device security essential.
Look for Critical mobile security measures such use dedicated work devices separate from personal phones, disable location services for all non-essential applications and enable full-disk encryption with strong passphrases. It is also advisable to Implement remote wipe capabilities for devices that may be captured.
Work computers require specialized configurations for conflict zone operations. Dedicated work computers should sacrifice convenient features like Bluetooth and USB ports for enhanced security.
Follow the essential computer security setup:
Open-source intelligence has become an essential tool for identifying and responding to cyber threats in relation to geopolitical events, enabling activists and journalists to connect geopolitical events to actionable steps through the Event-Action Chain framework that links incidents to vulnerabilities, threats, risks, and responses.
Professional threat intelligence involves analyzing reports from government agencies, international organizations, scientific publications, and credible media sources, while conducting thorough analysis of cybersecurity reports issued by government agencies, security consultancies, and cybersecurity organizations.
Forensic analysis employs four critical steps: write-blocking to prevent evidence tampering, mounting images for analysis, manual browsing through directories, and processing through professional forensics packages. Sandboxing provides an excellent method for analyzing malware behavior and observing outbound connections, processes running in background, registry changes, and other payloads downloaded in isolated environments.
Advanced forensic techniques include reverse steganography and file carving to tap into hidden data through specialized International Organization for Standardization guidelines, while forensic software identifies malware’s nature, functionality, and origins, providing vital intelligence on attackers’ techniques.
OPSEC is a risk-management process that identifies critical information and actively protects it from adversaries through five key analytical questions: what to protect, who to protect it from, likelihood of threats, consequences of failure, and acceptable security trade-offs. Implementation requires detecting sensitive information including client data, financial information, employee details, and intellectual property, then identifying potential threat matrices and analyzing vulnerabilities in security operations. Modern OPSEC strategies incorporate AI-powered risk scoring, continuous monitoring of user behavior, and identity-based access controls, with organizations using adaptive insider risk models.
Infrastructure hardening works by condensing attack surfaces to reduce security vulnerabilities, eliminating redundant programs, ports, applications, and access points to prevent hackers from penetrating systems easily. Systems hardening involves audit of existing systems using penetration testing, vulnerability scanning, and configuration management tools, followed by strategic approaches that create phased remediation plans for biggest flaws
Traditional cloud storage services are inadequate for sensitive journalistic materials. Specialized services like GiraffeDoc provide enhanced end-to-end encryption with role-based access controls specifically for journalists.
Comprehensive backup strategy:
Protecting source identity and information requires specialized procedures beyond standard encryption. Digital Security Labs can provide forensic analysis if source protection may have been compromised. Advanced source protection includes:
International humanitarian law provides specific protections for journalists in conflict zones under Article 79 of Additional Protocol I of the Geneva Conventions. These protections require that journalists be treated as civilians and protected accordingly, provided they take no direct part in hostilities. Key legal protections includes civilian status protection under international humanitarian law, freedom of expression rights under Articles 19 of the Universal Declaration of Human Rights and UN Security Council Resolution 2222 extending protections for media workers
However, extensive research reveals no binding and enforceable laws specifically addressing journalists’ digital rights, creating gaps in protection that make technical security measures even more critical.
Effective risk assessment involves analyzing five key questions: What am I protecting? Who am I protecting it from? How likely are these threats? What are the consequences of failure? How much trouble am I willing to go through?
Comprehensive threat modeling should consider the following factors:
When security incidents occur, rapid response is crucial. Organizations like the Associated Press use real-time alerting systems to protect journalists in conflict zones, demonstrating the importance of systematic incident response.
Apply the following Essential incident response steps:
Digital defense in conflict zones requires a comprehensive, layered approach combining technical security measures with operational discipline and legal awareness. With over 50% of journalist killings occurring in crisis and conflict zones, and digital threats increasing exponentially, robust cybersecurity is no longer optional, it’s essential for survival and operational effectiveness.
The investment in digital security infrastructure pays dividends not only in personal safety but in maintaining the integrity of journalism itself. Every year, hundreds of journalists are killed or imprisoned for their reporting, with thousands more facing surveillance and censorship. By implementing these digital defense strategies, journalists and activists can continue their critical work while minimizing risks to themselves, their sources, and their organizations.







Day 1257
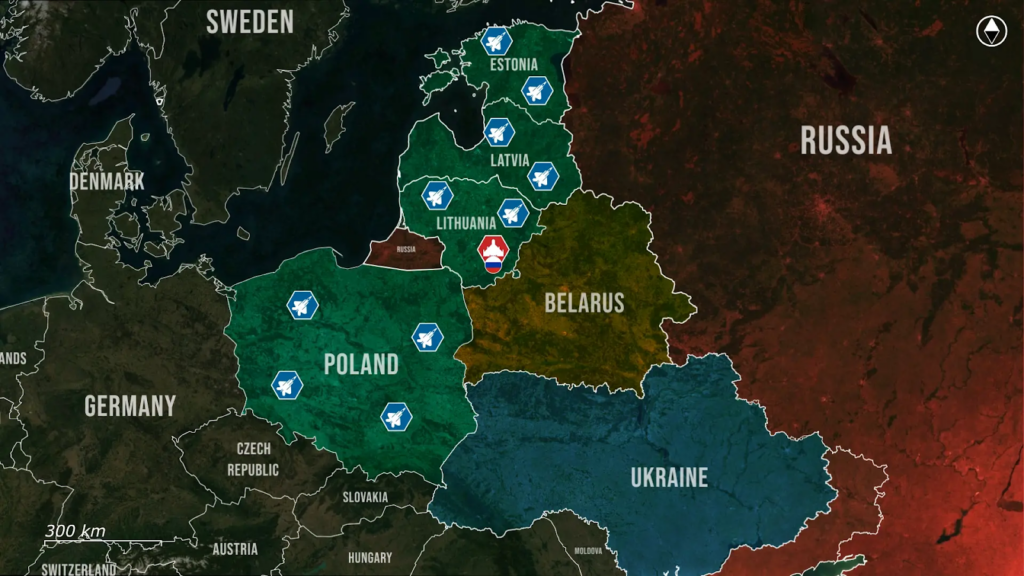
On 3 August, the biggest news comes from Eastern Europe.
Here, a Shahed-type drone flew directly into Lithuanian airspace and passed over the capital, marking a serious escalation in Russia’s aerial provocations against Nato’s eastern flank. Poland’s air force is already on a nightly high alert, and now the rest of the Baltics are joining in, raising what increasingly resembles an iron Curtain in the air.
Recently, a Russian Shahed-like drone crossed into Lithuanian airspace from Belarus and flew over the outskirts of Vilnius, the capital of Lithuania, close enough for civilians to see and film the device in flight. Initial fears suggested a live munition had entered Nato airspace, as Shaheds are often fitted with fragmentation, thermobaric, incendiary, or delayed-fuse warheads to cause maximum casualties and damage to civilian property.

Fortunately, upon further inspection of the video footage, the object was identified as a Gerbera decoy drone, a visually similar platform Russia uses for both reconnaissance and saturation purposes during their daily strikes on Ukrainian cities.
While unarmed, the drone crossed directly over a Nato capital, far from any logical flight path to Ukraine, making it clear that this was no accident.
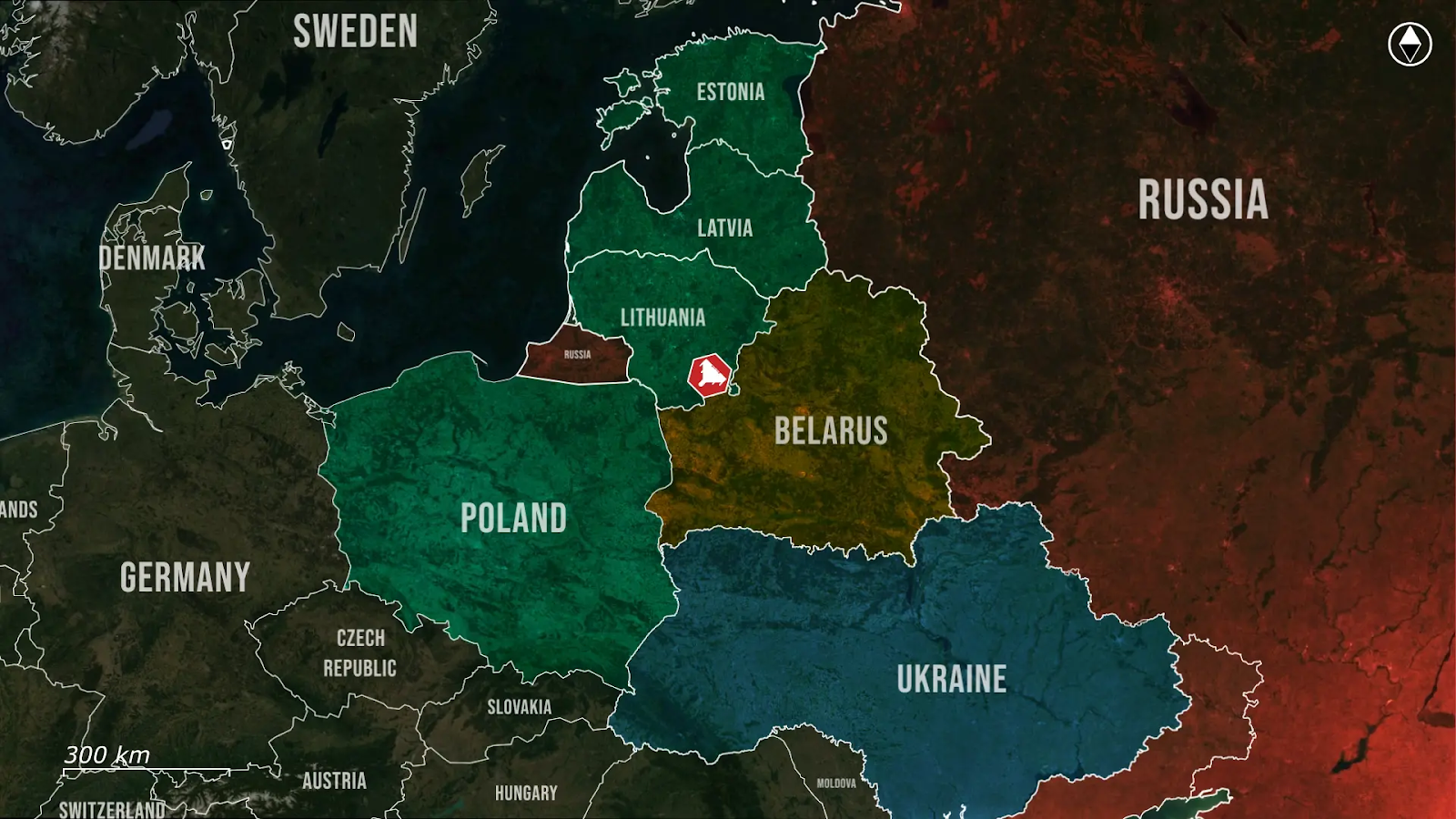
Instead, it was a calculated decision to test Nato’s reaction time, radar coverage, and political tolerance for such direct aerial threats and provocations, and critically, Lithuanian forces did not intercept.
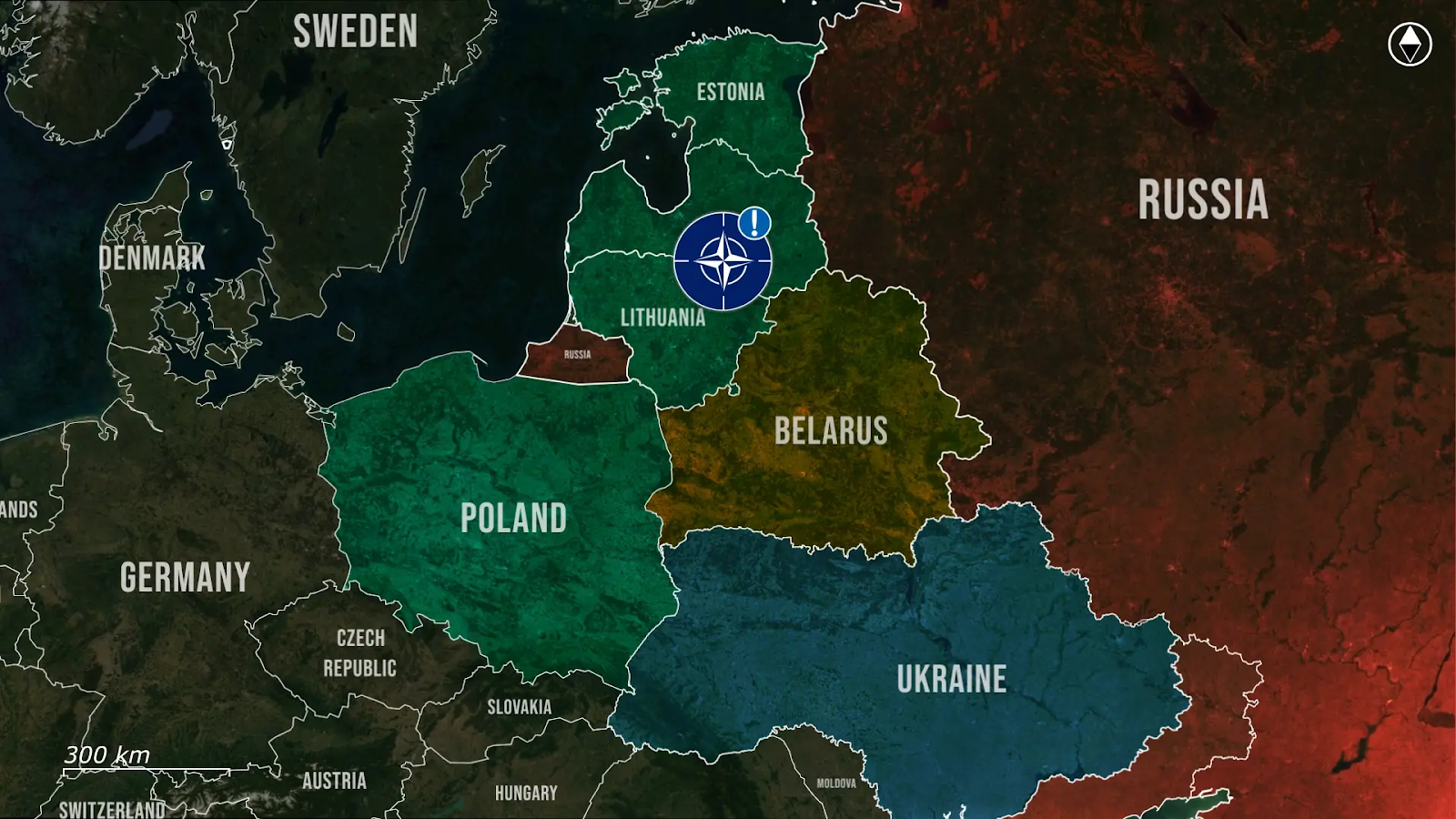
Poland, meanwhile, has entered a state of routine high alert, with Polish and Nato forces scrambling jets and raising radar systems every time Russia launches a large-scale assault on Ukraine, which happens every night and now often even during the day as well. Nato partners, including Swedish Gripens, are now joining Poland in maintaining a high alert status during Russia’s large-scale drone and missile attacks on Ukraine, reinforcing joint readiness across the eastern flank. While these alerts are precautionary, they have become the new norm, as the Polish border lies directly behind the approach paths of Russian missiles and drones targeting western Ukrainian cities. This proximity means any technical malfunction or mid-course deviation could result in a direct violation of Polish airspace, as seen in previous incidents, including when debris from Russian missiles entered Polish territory in 2022, or when a Ukrainian air defense missile landed on a Polish field, killing two farmers.
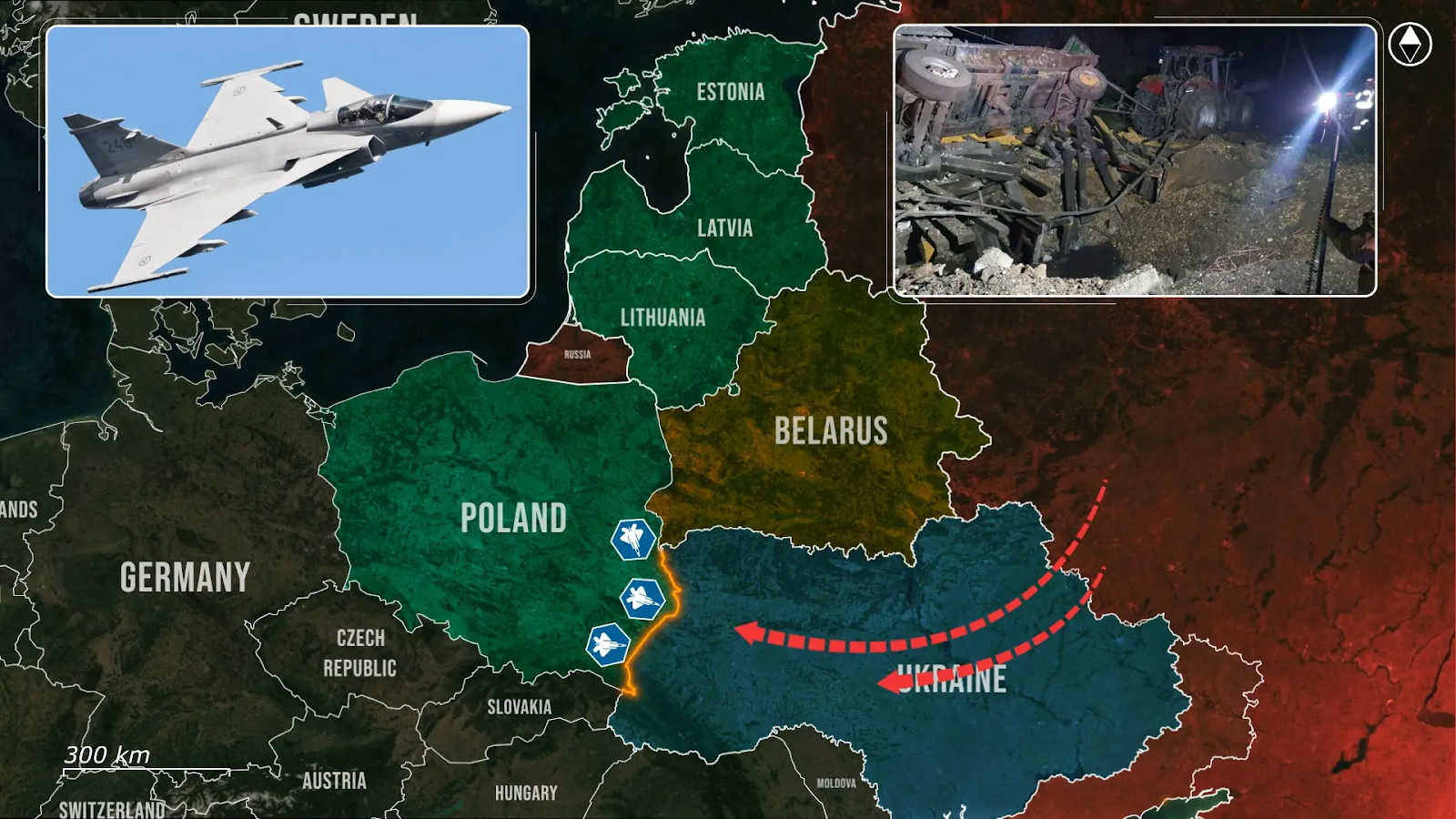
Unlike the calculated provocation over Vilnius, Poland faces a more constant strain of nightly threats, scrambling fighters, activating radar grids, and maintaining alert in civilian areas without knowing whether each launch might cause military objects to cross into its airspace. Across the Baltics, Lithuania, Latvia, and Estonia have long depended on Nato’s Baltic Air Policing mission, with Hungary, Italy, and Spain being part of the current rotation, maintaining quick-reaction alert status and integrated into Nato’s broader air defense system.
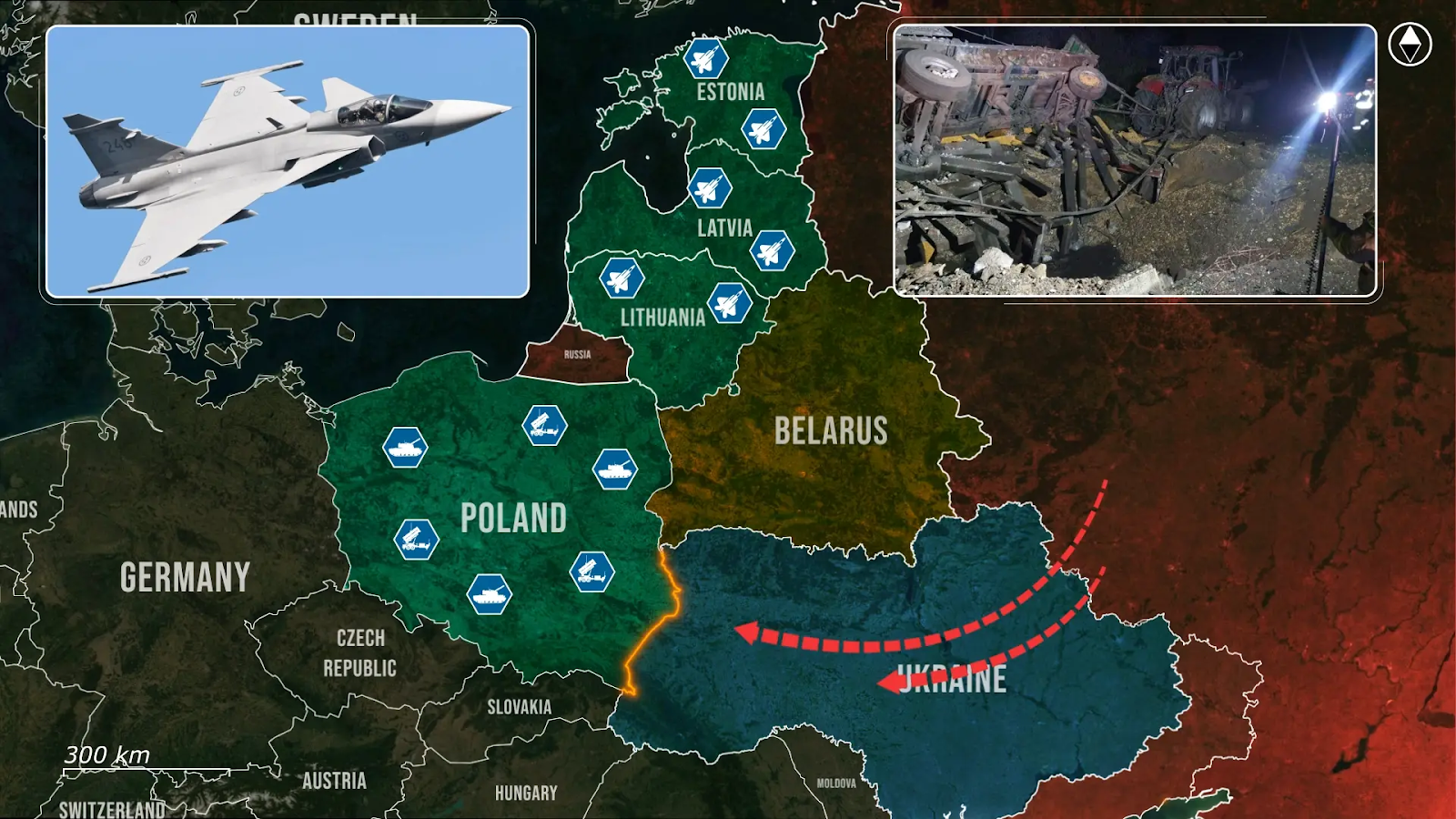
However, the unchallenged drone over Vilnius shows the limits of deterrence alone, and Lithuania is now accelerating the deployments of Ukrainian-developed acoustic drone detection systems, seeking to fill gaps in its early warning networks exposed by the most recent airspace violation.
At the same time, the Baltic states are reinforcing their readiness for both air-to-air and ground-to-air engagements by expanding joint training protocols, adapting quick-reaction procedures, and integrating new detection systems designed to counter the threat of low-flying unmanned platforms.

And across all three states, radar tracking, jamming incidents logs, and drone incursions are now analyzed with a single assumption: that any aerial anomaly could be the opening in a broader conflict. The emerging posture is no longer passive monitoring; with new drone detection systems, joint alert protocols, and revised civilian flight corridors, it is becoming forward-leaning, reinforced, and increasingly closed, an Iron Curtain in the air.

Overall, Russia’s latest airspace violations are increasingly escalating and reshaping Nato’s eastern defenses through repeated, calculated provocations that expose gaps, test thresholds, and force reaction. The incursion over Vilnius is a template for how Moscow may continue to pressure Nato’s eastern flank, trying to provoke member states into triggering an open conflict. As Poland’s nightly alerts become routine and Baltic air defenses are forced to harden, the question is no longer whether Nato will respond, but how far that response will go, and as this pattern deepens, the skies over Eastern Europe are no longer a buffer, they are becoming the front line.
In our regular frontline report, we pair up with the military blogger Reporting from Ukraine to keep you informed about what is happening on the battlefield in the Russo-Ukrainian war
You could close this page. Or you could join our community and help us produce more materials like this.
We keep our reporting open and accessible to everyone because we believe in the power of free information. This is why our small, cost-effective team depends on the support of readers like you to bring deliver timely news, quality analysis, and on-the-ground reports about Russia's war against Ukraine and Ukraine's struggle to build a democratic society.
Become a patron or see other ways to support.



White House official says India ‘basically tied with China in purchasing Russian oil’ as Delhi defies sanctions threat

© AFP via Getty

Ukraine has unleashed hell on the occupiers. During the night of 4 August, Ukrainian drones launched a powerful strike on a Russian-occupied airbase in Crimea. One of Russia’s most advanced tactical fighter jets was completely destroyed, and four more aircraft were hit, the Security Service (SBU) reports.
Russian aircraft based near Ukraine is capable of carrying guided bombs. In 2025, Russia plans to produce 75,000 aerial bombs equipped with glide and correction modules, which turn a standard unguided bomb into a precision-guided munition with an extended range. The new number represents Moscow’s plans for a 50% increase in guided bombs production output.
The target of the operation was one of Russia’s main airbases in temporarily occupied Crimea, the Saky military airfield, from which enemy planes take off to strike southern Ukraine and ships in the Black Sea. The base hosts strategic bombers and reconnaissance aircraft. The airfield lies nearly 70-80 kilometers from Ukraine-controlled territory.
The SBU’s “Alpha” Special Center used drones to deliver precision strikes on Russian equipment. As a result of the special operation:
A warehouse containing aviation munitions was incinerated.
The Russians lost at least one Su-30SM, valued at $50 million. These fighters can carry up to 8 tons of bombs and missiles and have a combat radius of up to 1,500 km.
Several Su-24 aircraft were also damaged. These are used for precision strikes on ground targets, with a combat radius of around 560 km. Russia’s losses may reach tens of millions of dollars.
The Security Service of Ukraine confirmed the strike, emphasizing that the operation is a key part of the strategy to destroy enemy logistics and combat capabilities in Crimea.
“Occupiers must remember they will never feel safe on our land!” the SBU stated.

Thanks to your incredible support, we’ve raised 70% of our funding goal to launch a platform connecting Ukraine’s defense tech with the world – David vs. Goliath defense blog. It will support Ukrainian engineers who are creating innovative battlefield solutions and we are inviting you to join us on the journey.
Our platform will showcase the Ukrainian defense tech underdogs who are Ukraine’s hope to win in the war against Russia, giving them the much-needed visibility to connect them with crucial expertise, funding, and international support.
We’re one final push away from making this platform a reality.




Russia’s position on Ukraine remains unchanged. The Kremlin states it does not rule out a meeting between Russian President Vladimir Putin and Ukrainian leader Volodymyr Zelenskyy but only after extensive preparatory work at the expert level, UNIAN reports.
In practice, Putin does not recognize the Ukrainian government as legitimate and is unwilling to negotiate without full compliance with his demands — which effectively amount to Ukraine’s capitulation.
“Putin is ready to meet with Zelenskyy after preparatory work at the expert level. However, that work has not been carried out yet,” Dmitry Peskov, the Kremlin’s spokesperson, told Russian media.
Russia’s demands, unchanged since summer 2024, include: official recognition of annexed territories, guarantees of Ukrainian neutrality, demilitarization, and a pledge not to join NATO. Moscow insists that only after these conditions are met can any serious talks take place.
Putin shrugs off Trump’s ultimatum and says he’s ready to wait until Kyiv agrees to his conditions to end war
Currently, global observers are watching closely to see whether US President Donald Trump will impose sanctions after the Kremlin refused to comply with his ceasefire ultimatum on Ukraine.
After former Russian President Dmitry Medvedev’s claims, referencing the Soviet automatic nuclear strike system “Dead Hand” in the context of threats against the US, Trump ordered the deployment of two nuclear submarines. Medvedev’s threats came following Trump’s announcement of a 10-day ultimatum that the US gave to Russia to end its war.
This exchange significantly escalated nuclear rhetoric between the two powers, underscoring the growing intertwining of the Ukraine war with nuclear deterrence.

President Donald Trump revealed on 3 August that American nuclear submarines have moved into position near Russian waters, confirming the deployment he ordered just days earlier in response to escalating threats from Moscow.
“They are in the region, yeah, where they have to be,” Trump told reporters when asked about the submarine positioning, according to The Hill.
The submarine deployment represents Trump’s most direct military response yet to what he called “highly provocative statements” from Dmitry Medvedev, Russia’s former president who now serves as Deputy Chairman of the Security Council.
The military positioning follows Trump’s 10-day ultimatum to Russia over the Ukraine war. Trump threatened tariffs and sanctions unless Moscow shows progress ending the war.
Medvedev fired back, accusing Trump of “playing a game of ultimatums with Russia.” The Russian official warned that “every new ultimatum is a threat and a step toward war” – targeting not Ukraine, but Trump’s “own country.”
On 31 July, Trump told Medvedev to “watch his words” and calling him a “failed former President of Russia, who thinks he’s still President.”
“He’s entering very dangerous territory!” Trump declared, noting that “Russia and the USA do almost no business together. Let’s keep it that way.”
Medvedev responded by invoking Russia’s “Dead Hand” nuclear system and telling Trump to “remember his favorite zombie movies.”
On 1 August, Trump announced his submarine deployment on Truth Social: “I have ordered two Nuclear Submarines to be positioned in the appropriate regions, just in case these foolish and inflammatory statements are more than just that.”
Words are very important, and can often lead to unintended consequences, I hope this will not be one of those instances,” he added.
Kremlin spokesman Dmitry Peskov downplayed the submarine news, telling Russian media that “American submarines are already on combat duty anyway. This is a constant process.”
But Peskov stressed Russia’s careful approach to nuclear rhetoric: “We are very careful about any statements related to nuclear issues. Russia takes a responsible position.”
When pressed about Medvedev’s inflammatory statements, Peskov deflected: “In every country, members of the country’s leadership have different views.” He emphasized that “President Putin” formulates Russia’s foreign policy.
Trump confirmed his special envoy Steve Witkoff will travel to Russia this week – either 6 or 7 August for talks ahead of planned new sanctions.
The diplomatic mission comes as nuclear-armed submarines patrol near Russian waters, creating a complex backdrop of military pressure and negotiation attempts.

Global tech giants come to Kyiv. Deputy Defense Minister Serhii Boiev has held talks in Kyiv with Axon founder and CEO Rick Smith and head of Dedrone by Axon, Aaditya Devarakonda, Ukraine’s Defense Ministry reports.
The integration of Ukrainian military technologies amid Russia’s war of attrition is becoming a key factor in the country’s survival. Ukrainian engineers are implementing real-time reconnaissance systems, artificial intelligence, and robotic unmanned platforms.
The main topic has been the joint fight against enemy UAVs (drones), technology exchange, and scaling production of electronic warfare tools and drone interceptors.
“We are most interested in electronic warfare (EW) technologies and drone interceptors,” says Boiev.
During the meeting, Axon CEO Rick Smith told the Ukrainian officials that “our offer is not about business but about protecting people.”
Axon is a US leader in public safety, known for TASER stun guns, body cameras, digital platforms, and evidence analysis software, used by police and security agencies in many countries.
Dedrone by Axon specializes in airspace protection from unauthorized drones. Its technology operates in over 50 countries — in prisons, stadiums, airports, and even military units.
Dedrone uses artificial intelligence and machine learning to detect, track, and neutralize drones. The system integrates data from radars, radio frequencies, and video cameras into a unified C2 platform — either local or cloud-based.
Kyiv already cooperates with domestic companies to ramp up production of drone countermeasure systems, but according to Boiev, they “continue searching for new solutions.”

Authorities in Sochi detained two girls and a young man who filmed a video against the backdrop of a burning oil depot, according to the Krasnodar Oblast Ministry of Internal Affairs.
The detainees traveled to Sochi from Nizhny Tagil, the ministry reported. Officials issued a protocol against one of the detained individuals under the article concerning “failure to comply with rules of conduct in case of emergency situation or threat of its occurrence.”
This violation carries penalties ranging from a warning to fines between 1,000 and 30,000 rubles ($12-$375).
Adler oil depot in Sochi, southern Russia, burned after Ukrainian drones struck overnight on 3 August, igniting a 2,000 cubic meter fuel tank around 530 km from the frontline. The strike forced a halt to flights at Sochi airport.
Telegram channels reported, citing eyewitnesses, that approximately 20 explosions were heard in Sochi. The oil depot includes 41 tanks with a combined capacity of around 31,200 cubic meters.