China Sees Gaps in U.S. Defenses, Ousted National Security Official Says

© Kenny Holston/The New York Times


© Kenny Holston/The New York Times


© Tatyana Makeyeva/Agence France-Press — Getty Images
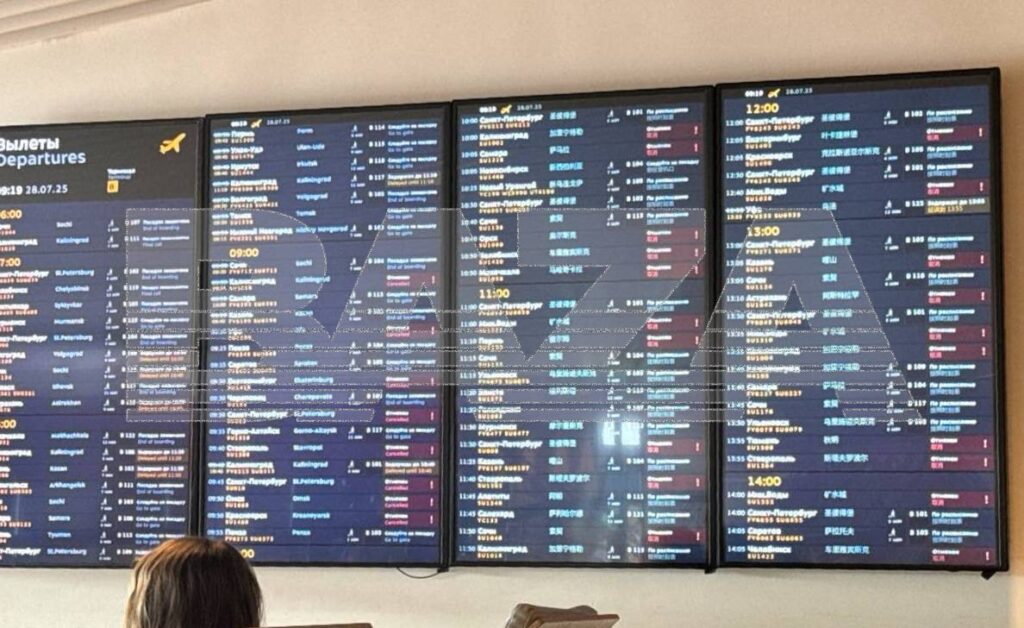

Pro-Ukrainian hackers launched a devastating cyberattack against Aeroflot, Russia’s government-owned flagship airline, canceling 50 flights and leaving hundreds of passengers stranded at Moscow airports on 28 July.
Two hacker groups claimed responsibility for a cyberattack that allegedly destroyed the carrier’s internal IT infrastructure.
The flight disruptions affected routes from Moscow’s Sheremetyevo airport to destinations including Minsk, Yerevan, Yekaterinburg, Kaliningrad, and St. Petersburg.
Chaos erupted at Moscow’s Sheremetyevo airport as hundreds of frustrated Aeroflot passengers found themselves trapped in a digital nightmare. After waiting hours for flights that would never depart, travelers discovered they couldn’t even leave the airport easily—bottlenecks formed at exit passages, forcing people to stand in line just to get out of the building.
Traffic jams clogged roads outside as passengers abandoned their travel plans en masse, with many unable to secure refunds since the airline’s systems were down and only call centers could process requests.
According to Russian Telegram channel Baza, the scene resembled a mass evacuation as Aeroflot representatives urged people with canceled flights to simply go home rather than wait at the airport, leaving travelers stranded with no clear timeline for when normal operations might resume or whether their money could be recovered.
Anti-Russian groups Silent Crow and Belarusian Cyber Partisans BY claimed they spent a year infiltrating the airline’s network before destroying approximately 7,000 servers, explicitly linking their attack to Russia’s war against Ukraine and signing off with “Glory to Ukraine! Long live Belarus!”
The hackers say they accessed 122 hypervisors and 43 virtualization systems. They allegedly copied 12 terabytes of flight databases, 8 terabytes of corporate files, and 2 terabytes of email. Personal data of every Russian who ever flew Aeroflot? Gone, according to their statement.
“All these resources are now inaccessible or destroyed, restoration will require possibly tens of millions of dollars. The damage is strategic,” the hackers stated in their message.
The attack’s immediate impact was evident in Aeroflot’s operations. According to Baza’s source within the airline, employees could not access flight plans, contact crew members, or determine aircraft locations.
One Aeroflot employee described the scene: “I came to work, but we can’t print flight plans, nobody knows anything. I can’t even find the crew number, can’t call the captain.”
The employee continued: “All planes are grounded, management knows nothing: where the plane is, who’s flying, where they’re flying, crew numbers. There’s absolutely nothing.”
Only flights with pre-calculated plans could depart. Everyone else waited. Some crews spent hours sitting in aircraft with no instructions. Many employees were simply sent home.
Russia’s General Prosecutor’s Office confirmed the disruption was a cyberattack, not technical failure, as the hackers promised to publish stolen personal data from every Russian who ever flew the country’s largest airline.
Pro-Ukrainian hackers brought down Russia's largest government-owned airline system on 28 July.
— Euromaidan Press (@EuromaidanPress) July 28, 2025
The hackers signed off their cyberattack with "Glory to Ukraine! Long live Belarus!"
The attack forced the cancellation of around 50 Aeroflot flights and left hundreds of… pic.twitter.com/Rxzy3Lgjgw
Here’s what makes this attack different: The hackers claim they maintained access for an entire year before striking. That’s not opportunistic hacking—that’s patient intelligence work. They allegedly penetrated what they call “Tier0” systems, the core infrastructure that keeps airlines running.
Why target an airline? The hackers were explicit. Their statement addressed Russian security services directly: “You are incapable of protecting even your key infrastructures.” They called it a message to “all employees of the repressive apparatus.”
The groups signed off with “Glory to Ukraine! Long live Belarus!”—making their allegiances clear.
The attack occurred as Russia’s aviation sector already struggles under international sanctions and limited access to Western aircraft and parts. Adding cyberattacks from Ukraine-aligned groups to that list creates a new vulnerability Moscow hadn’t fully considered.


© Associated Press


Ukrainian military intelligence cyber specialists have carried out a powerful operation against Russian authorities in occupied Crimea. According to RBC-Ukraine’s intelligence sources, the cyberattack lasted several days and paralyzed the entire digital infrastructure of the occupation administration.
Russia is transforming occupied Ukrainian regions into military bases. Moscow troops use Donetsk and Luhansk oblasts to build up combat units, establish fortified positions, and organize logistics hubs. Meanwhile, from occupied Crimea, Russian forces are launching missiles and drones at other Ukrainian cities.
It began with a powerful DDoS assault that took down the occupiers’ government services. While panic spread in Crimea and technicians scrambled to identify the source of the outage, Ukrainian hackers had already infiltrated the electronic accounts of the so-called “authorities.” And that was just the beginning.
The Ukrainian Defence Intelligence has gained access to the occupiers’ key digital systems:
In just two days, over 100 terabytes of classified information were downloaded. Among the documents were files marked as top secret, including data on military facilities and logistics for supplying Russian troops.
After completing the operation, HUR specialists destroyed all the occupiers’ administrative servers, at both regional and district levels. These structures have effectively lost access to their documents, databases, and internal communications.
“So much data was extracted that we’ll soon uncover plenty of sensational details about Russian crimes in Crimea. Special thanks for the assistance goes to the deputy minister of health of the occupation government, Anton Lyaskovsky,” an intelligence source told RBC-Ukraine with irony.
Moscow has already labeled the operation as “elements of hybrid warfare.” Meanwhile, the so-called “Ministry of Internal Policy” of Crimea has admitted that some services remain offline. However, the true scale of the destruction is only beginning to come to light.


© Tingshu Wang/Reuters


A Ukrainian cyberattack on Gazprom systems has reportedly crippled the Russian state gas monopoly’s digital infrastructure, Suspilne reports, citing a source in Ukraine’s Defense Intelligence (HUR). The hackers wiped data from physical servers, cloud platforms, and all backups, targeting critical control systems that manage Russia’s gas flows, finances, and internal operations.
Suspilne reported earlier that the attack took place on 17 July. Now, Suspilne’s HUR source said Ukraine’s intelligence operatives obtained full access to all of Gazprom’s information systems, reaching a depth of penetration that the source described as “unprecedented.” The access reportedly included internal analytics, core servers, digital platforms, and user credentials from across Gazprom’s operational hierarchy.
According to Suspilne’s reporting, the operation began with full infiltration and ended with a coordinated deletion of all available data — including security systems, server control modules, and support networks that kept Gazprom’s infrastructure running.

Suspilne reports that more than 390 subsidiaries and branches were affected, including Gazprom Teplo Energo, Gazprom Obl Energo, and Gazprom Energosbyt. The breach extended into Gazprom’s SCADA and GIS systems, which control gas and oil pressure, distribution flows, well data, and infrastructure networks.
The HUR source also claimed that Gazprom’s financial records, tax data, contract logs, and legal documents were destroyed. Among the deleted systems were modules managing supply schedules, customer volumes, tariffs, payments, licensing, and regulatory files.

The scale of the operation, Suspilne’s source stated, could lead to a partial or total collapse in Gazprom’s ability to function. Without operational systems, the state corporation may be unable to sign new contracts, manage its gas supply network, or maintain stable financial operations.
The source further suggested that the consequences could include regional disruptions to gas transport and delivery, a potential default on corporate obligations, and sharp devaluation of Gazprom’s stock, possibly triggering instability in banks that finance the energy conglomerate.
Using custom-developed software, Ukrainian cyber operatives reportedly deleted all data stored on Gazprom’s physical servers and cloud infrastructure, including backup copies.


A global law enforcement campaign has dealt a blow to the pro-Russian cyber army known as NoName057(16). Europol confirmed that about 20 countries helped dismantle the network behind thousands of attacks on Ukraine’s supporters.
Europol reported that between 14 and 17 July, authorities from 12 countries launched Operation Eastwood. Europol and Eurojust coordinated the joint crackdown. The effort reportedly dismantled major parts of the pro-Russian cyber army’s infrastructure, including hundreds of systems.
Germany issued six arrest warrants for suspects based in Russia. Two are accused of leading the group’s activities. Spain issued another arrest warrant. France and Spain also reported one arrest each. All suspects are internationally wanted.
Authorities carried out 24 house searches and questioned 13 individuals across Europe. In Spain alone, 12 searches took place. Investigators also notified over 1,000 individuals believed to support the cyber group. Fifteen of them were administrators.
Other attacks struck during the European elections. Swedish government and banking websites were affected. In Switzerland, NoName057(16) launched attacks in June 2023, during a speech by Ukraine’s president to the Joint Parliament. Another wave occurred in June 2024 during the Peace Summit for Ukraine at Bürgenstock.
The most recent attack linked to the group targeted the NATO summit held in the Netherlands in June 2025. Europol notes that although the attacks caused disruption attempts, none led to substantial outages.
Europol identifies NoName057(16) as an ideological cyber network that operated without formal leadership. The group recruited mostly Russian-speaking sympathizers, many with little technical knowledge. Its structure relied heavily on gamified propaganda and incentives.
Volunteers received cryptocurrency payments and recognition through online shout-outs, badges, and leaderboards. Europol notes this method especially appealed to younger users who felt emotionally involved in Russia’s political narratives.
To simplify participation, NoName057(16) distributed guides and tools like DDoSia. Europol also launched a prevention campaign warning suspected supporters of their criminal liability, delivered via the same communication platforms.