DHS Is Deploying a Powerful Surveillance Tool at College Football Games

A version of this article was previously published on FOIAball, a newsletter reporting on college football and public records. You can learn more about FOIAball and subscribe here.
Last weekend, Charleston’s tiny private military academy, the Citadel, traveled to Ole Miss.
This game didn’t have quite the same cachet as the Rebels' Week 11 opponent this time last year, when a one-loss Georgia went to Oxford.
A showdown of ranked SEC opponents in early November 2024 had all eyes trained on Vaught-Hemingway Stadium.
Including those of the surveillance state.
According to documents obtained by FOIAball, the Ole Miss-Georgia matchup was one of at least two games last year where the school used a little-known Department of Homeland Security information-sharing platform to keep a watchful eye on attendees.
The platform, called the Homeland Security Information Network (HSIN), is a centralized hub for the myriad law enforcement agencies involved with security at big events.
According to an Event Action Plan obtained by FOIAball, at least 11 different departments were on the ground at the Ole Miss-Georgia game, from Ole Miss campus police to a military rapid-response team.
HSINs are generally depicted as a secure channel to facilitate communication between various entities.
In a video celebrating its 20th anniversary, a former HSIN employee hammered home that stance.“When our communities are connected, our country is indeed safer," they said.
In reality HSIN is an integral part of the vast surveillance arm of the U.S. government.
Left unchecked since 9/11, supercharged by technological innovation, HSIN can subject any crowd to almost constant monitoring, looping in live footage from CCTV cameras, from drones flying overhead, and from police body cams and cell phones.
HSIN has worked with private businesses to ensure access to cameras across cities; they collect, store, and mine vast amounts of personal data; and they have been used to facilitate facial recognition searches from companies like Clearview AI.
It’s one of the least-reported surveillance networks in the country.
And it's been building this platform on the back of college football.
Since 9/11, HSINs have become a widely used tool.

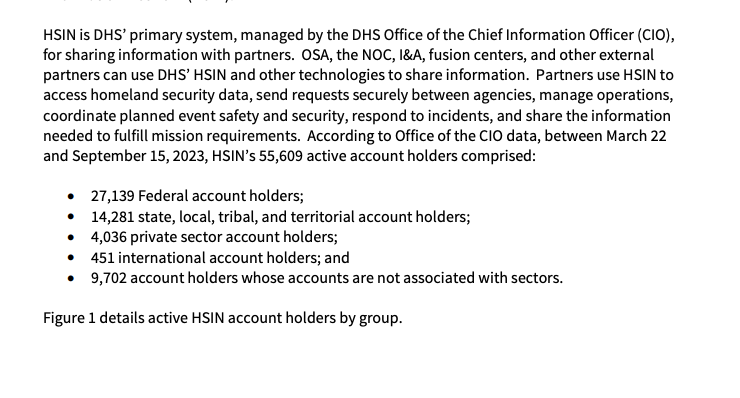
A recent Inspector General report found over 55,000 active accounts using HSIN, ranging from federal employees to local police agencies to nebulous international stakeholders.
The platforms host what’s called SBU, sensitive but unclassified information, including threat assessments culled from media monitoring.
According to a privacy impact study from 2006, HSIN was already maintaining a database of suspicious activities and mining those for patterns.
"The HSIN Database can be mined in a manner that identifies potential threats to the homeland or trends requiring further analysis,” it noted.
In an updated memo from 2012 discussing whose personal information HSIN can collect and disseminate, the list includes the blanket, “individuals who may pose a threat to the United States.”


A 2023 DHS “Year in Review” found that HSIN averaged over 150,000 logins per month.
Its Connect platform, which coordinates security and responses at major events, was utilized over 500 times a day.
HSIN operated at the Boston Marathon, Lollapalooza, the World Series, and the presidential primary debates. It has also been used at every Super Bowl for the last dozen years.
DHS is quick to tout the capabilities of HSINs in internal communications reviewed by FOIAball.
In doing so, it reveals the growth of its surveillance scope. In documents from 2018, DHS makes no mention of live video surveillance.
But a 2019 annual review said that HSINs used private firms to help wrangle cameras at commercial businesses around Minneapolis, which hosted the Final Four that year.
“Public safety partners use HSIN Connect to share live video streams from stationary cameras as well as from mobile phones,” it said. “[HSIN communities such as] the Minneapolis Downtown Security Executive Group works with private sector firms to share live video from commercial businesses’ security cameras, providing a more comprehensive operating picture and greater situational awareness in the downtown area.”
And the platform has made its way to college campuses.
Records obtained by FOIAball show how pervasive this technology has become on college campuses, for everything from football games to pro-Palestinian protests.
In November 2023, students at Ohio State University held several protests against Israel’s war in Gaza. At one, over 100 protesters blocked the entrance to the school president’s office.
A report that year from DHS revealed the protesters were being watched in real-time from a central command center.
Under the heading "Supporting Operation Excellence," DHS said the school used HSIN to surveil protesters, integrating the school’s closed-circuit cameras to live stream footage to HSIN Connect.
“Ohio State University has elevated campus security by integrating its closed-circuit camera system with HSIN Connect,” it said. “This collaboration creates a real-time Common Operating Picture for swift information sharing, enhancing OSU’s ability to monitor campus events and prioritize community safety.”
“HSIN Connect proved especially effective during on-campus protests, expanding OSU’s security capabilities,” the school’s director of emergency management told DHS. “HSIN Connect has opened new avenues for us in on-campus security.”
While it opened new avenues, the platform already had a well-established relationship with the school.
According to an internal DHS newsletter from January 2016, HSIN was utilized at every single Buckeyes home game in 2015.
“HSIN was a go-to resource for game days throughout the 2015 season,” it said.
It highlighted that data was being passed along and analyzed by DHS officials.
The newsletter also revealed HSINs were at College Football Playoff games that year and have been in years since. There was no mention of video surveillance at Ohio State back in 2015. But in 2019, that capability was tested at Georgia Tech.
There, police used “HSIN Connect to share live video streams with public safety partners.”
A 2019 internal newsletter quoted a Georgia Tech police officer about the use of real-time video surveillance on game days, both from stationary cameras and cell phones.
“The mobile app for HSIN Connect also allows officials to provide multiple, simultaneous live video streams back to our Operations Center across a secure platform,” the department said.
Ohio State told FOIAball that it no longer uses HSIN for events or incidents. However, it declined to answer questions about surveilling protesters or football games.
Ohio State’s records department said that it did not have any documents relating to the use of HSIN or sharing video feeds with DHS.
Georgia Tech’s records office told FOIAball that HSINs had not been used in years and claimed it was “only used as a tool to share screens internally." Its communications team did not respond to a request to clarify that comment.
Years later, DHS had eyes both on the ground and in the sky at college football.
According to the 2023 annual review, HSIN Connect operated during University of Central Florida home games that season. There, both security camera and drone detection system feeds were looped into the platform in real-time.

DHS said that the "success at UCF's football games hints at a broader application in emergency management.”
HSIN has in recent years been hooked into facial recognition systems.
A 2024 report from the U.S. Commission on Civil Rights found that the U.S. Marshals were granted access to HSIN, where they requested "indirect facial recognition searches through state and local entities" using Clearview AI.
Which brings us to the Egg Bowl—the annual rivalry game between Ole Miss and Mississippi State.
FOIAball learned about the presence of HSIN at Ole Miss through a records request to the city’s police department. It shared Event Action Plans for the Rebels’ games on Nov. 9, 2024 against Georgia and Nov. 30, 2024 against Mississippi State.
It’s unclear how these partnerships are forged.
In videos discussing HSIN, DHS officials have highlighted their outreach to law enforcement, talking about how they want agencies onboarded and trained on the platform. No schools mentioned in this article answered questions about how their relationship with DHS started.
The Event Action Plan provides a fascinating level of detail that shows what goes into security planning for a college football game, from operations meetings that start on Tuesday to safety debriefs the following Monday.
Its timeline of events discusses when Ole Miss’s Vaught-Hemingway Stadium is locked down and when security sweeps are conducted. Maps detail where students congregate beforehand and where security guards are posted during games.
The document includes contingency plans for extreme heat, lightning, active threats, and protesters. It also includes specific scripts for public service announcers to read in the event of any of those incidents.
It shows at least 11 different law enforcement agencies are on the ground on game days, from school cops to state police.
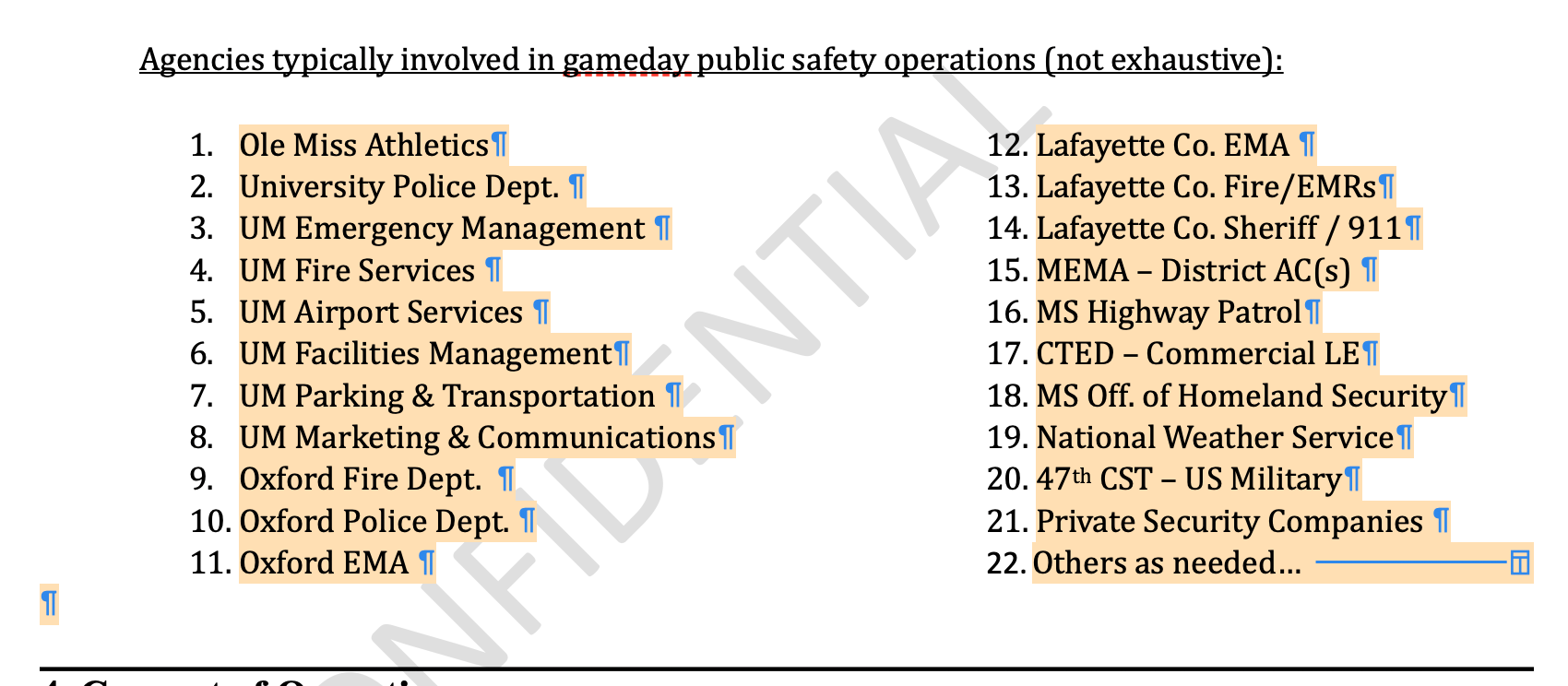
They even have the U.S. military on call. The 47th Civil Support Team, based out of Jackson Air National Guard Base, is ready to respond to a chemical, biological, or nuclear attack.
All those agencies are steered via the document to the HSIN platform.
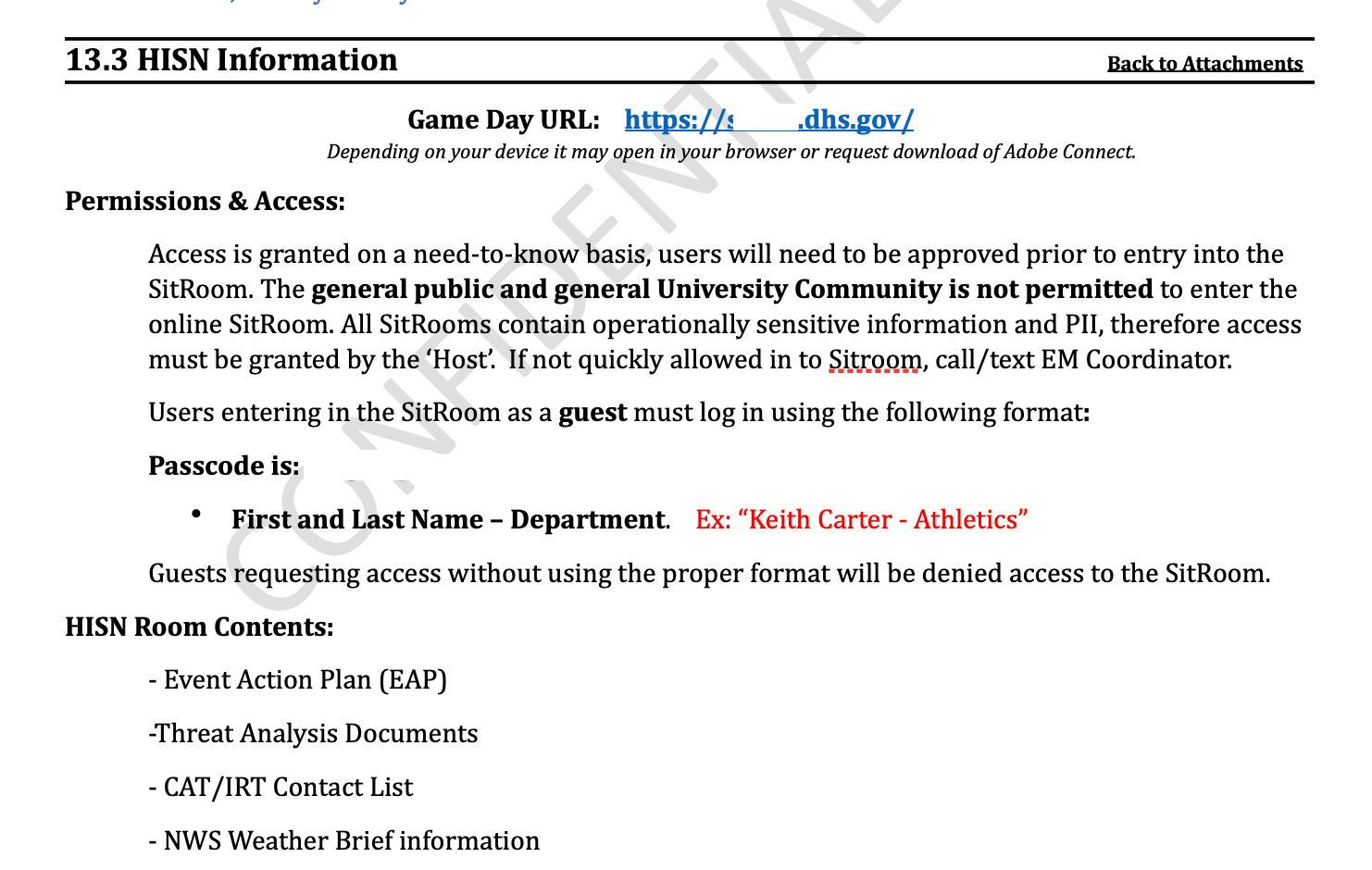
Under a section on communications, it lists the HSIN Sitroom, which is “Available to all partners and stakeholders via computer & cell phone.”
The document includes a link to an HSIN Connect page.
It uses Eli Manning as an example of how to log in.
“Ole Miss Emergency Management - Log in as a Guest and use a conventional naming convention such as: ‘Eli Manning - Athletics.’”

On the document, it notes that the HSIN hosts sensitive Personally Identifiable Information (PII) and Threat Analysis Documents.
“Access is granted on a need-to-know basis, users will need to be approved prior to entry into the SitRoom.”
“The general public and general University Community is not permitted to enter the online SitRoom,” it adds. “All SitRooms contain operationally sensitive information and PII, therefore access must be granted by the ‘Host’.”
It details what can be accessed in the HSIN, such as a chat window for relaying information.
It includes a section on Threat Analysis, which DHS says is conducted through large-scale media monitoring.
The document does not detail whether the HSIN used at Ole Miss has access to surveillance cameras across campus.
But that may not be something explicitly stated in documents such as these.
Like Ohio State, UCF told FOIAball that it had no memoranda of understanding or documentation about providing access to video feeds to HSINs, despite DHS acknowledging those streams were shared. Ole Miss’ records department also did not provide any documents on what campus cameras may have been shared with DHS.
While one might assume the feeds go dark after the game is over, there exists the very real possibility that by being tapped in once, DHS can easily access them again.
“I’m worried about mission creep,” Matthew Guariglia, a senior policy analyst at the Electronic Frontier Foundation, told FOIAball. “These arrangements are made for very specific purposes. But they could become the apparatus of much greater state surveillance.”
For Ole Miss, its game against Georgia went off without any major incidents.
Well, save for one.

During the second quarter, a squirrel jumped onto the field, and play had to be stopped.
In the EAP, there was no announcer script for handling a live animal interruption.

