Members of a congressional committee have demanded Department of Homeland Security (DHS) Secretary Kristi Noem for more information about Mobile Fortify, Immigration and Customs Enforcement’s (ICE) new facial recognition app, which taps into an unprecedented array of government databases and uses a system ordinarily reserved for when people enter or exit the U.S. 404 Media first revealed the app in June.
The Democratic lawmakers, Bennie G. Thompson, J. Luis Correa, and Shri Thanedar, are asking Noem a host of questions about the app, including what databases Mobile Fortify searches, the tool’s accuracy, and ICE’s legal basis for using the app to identify people outside of ports of entry, including U.S. citizens.
“Congress has long had concerns with the Federal government’s use of facial recognition technology and has regularly conducted oversight of how DHS utilizes this technology. The Mobile Fortify application has been deployed to the field while still in beta testing, which raises concerns about its accuracy,” the letter from the Committee on Homeland Security and addressed to Noem reads.
💡
Do you know anything else about this app? I would love to hear from you. Using a non-work device, you can message me securely on Signal at joseph.404 or send me an email at joseph@404media.co.
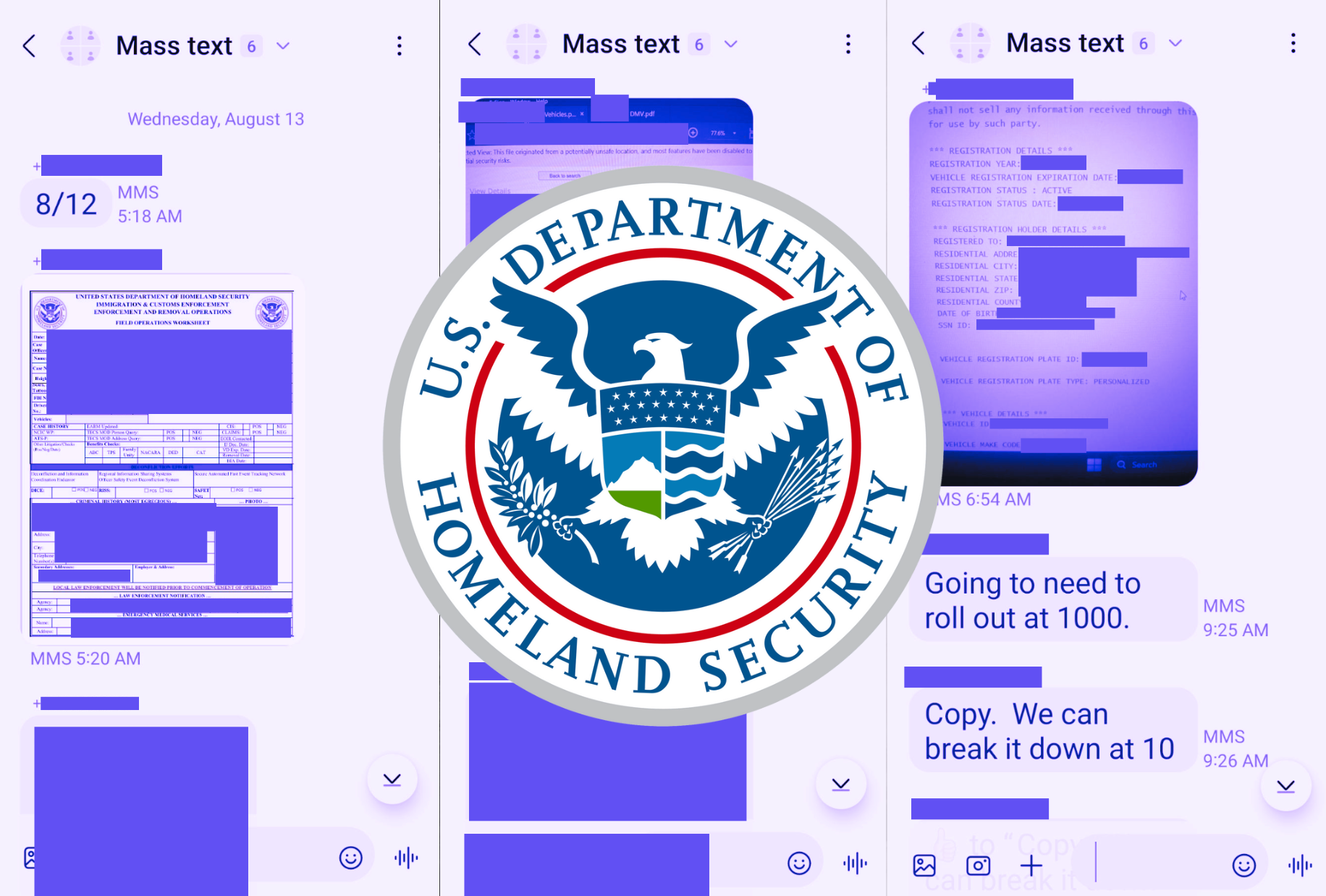
404 Media first revealed Mobile Fortify’s existence through leaked emails. Those emails showed that ICE officers could use the app to identify someone based on their fingerprints or face by just pointing a smartphone camera at them. The underlying Customs and Border Protection (CBP) system for the facial recognition part of the app is ordinarily used when people enter or leave the U.S. With Mobile Fortify, ICE then turned that capability inwards to identify people away from ports of entry.
In the footnotes of the letter, the lawmakers indicate they have a copy of a similar email, and the letter specifically cites 404 Media’s reporting.
In July 404 Media published a second report based on a Mobile Fortify user manual which explained the app’s capabilities and data sources in more detail. It said that Mobile Fortify uses a bank of 200 million images, and can pull up a subject’s name, nationality, date of birth, “alien” number, and whether a judge has marked them for deportation. It also showed that Mobile Fortify links databases from the State Department, CBP, the FBI, and states into a single tool. A “super query” feature lets ICE officers query multiple databases at once regarding “individuals, vehicles, airplanes, vessels, addresses, phone numbers and firearms.”
“Face recognition technology is notoriously unreliable, frequently generating false matches and resulting in a number of known wrongful arrests across the country. Immigration agents relying on this technology to try to identify people on the street is a recipe for disaster. Congress has never authorized DHS to use face recognition technology in this way, and the agency should shut this dangerous experiment down,” Nathan Freed Wessler, deputy director of the American Civil Liberties Union’s Speech, Privacy, and Technology Project, previously told 404 Media.
In their letter the lawmakers ask Noem questions about the app’s legality, including ICE’s legal basis to use the app to conduct biometric searches on people outside ports of entry; the databases Mobile Fortify has access to; any agreements between CBP and ICE about the app; information about the usage of the app, such as the frequency of ICE searches using the tool and what procedures ICE officials follow with the app; the app’s accuracy; and any policies or training to ICE agents on how to use the app.
“To ensure ICE is equipped with technology that is accurate and in compliance with constitutional and legal requirements, the Committee on Homeland Security is conducting oversight of ICE’s deployment of the Mobile Fortify application,” the letter says.
CBP acknowledged a request for comment but did not provide a response in time for publication. ICE did not respond to a request for comment.
You can find a copy of the letter here.